2025-06-05 20:51:20
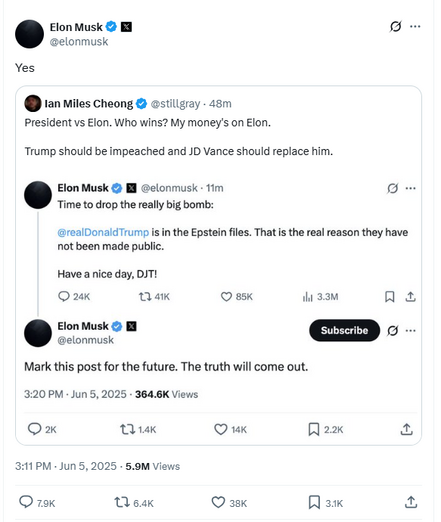
I think we all knew a Melon Husk / Turnip meltdown was inevitable, but I didn't think it'd happen this soon, escalate this quickly, or blowup this spectacularly.
🍿 🍿 🍿
#MelonHusk #POTUS47
2025-07-02 17:40:17
Teknologiakritiikin ja -kriitikoiden tarpeesta. Taiteessa on kriitikoilla ja kritiikillä tärkeä rooli. (...) Teknologian maailmassa ei juurikaan ole tuollaista kritiikkiä, vaan arviointi on analyysiä jostain näkökulmasta (...) No niin, voisi miettiä olisiko teknologiakritiikissä ideaa. Se voisi kohdistua suoraan teknologiaan, kuten tekoäly, tai teknologiahypetykseen. Sellaisen sisältöjä jälkimmäisessä tapauksessa olisivat esim.
Jatkuu...
2025-07-08 10:51:31
MoLink: Distributed and Efficient Serving Framework for Large Models
Lewei Jin, Yongqi Chen, Kui Zhang, Yifan Zhuo, Yi Gao, Bowei Yang, Zhengong Cai, Wei Dong
https://arxiv.org/abs/2507.05043
2025-06-06 07:16:35
Hiding in Plain Sight: Query Obfuscation via Random Multilingual Searches
Anton Firc, Jan Klus\'a\v{c}ek, Kamil Malinka
https://arxiv.org/abs/2506.04963
2025-06-25 06:10:49
Daydream, which raised a $50M seed in June 2024 to build a generative AI shopping agent for fashion, launches in beta, with an app expected later this summer (Hilary Milnes/Vogue Business)
https://www.voguebusiness.com/story/techno
2025-05-20 13:00:46
I decided to share some of my observations that would benefit you if you are building applications: a deep dive session into the archetypes of attackers.
This session is for people who are developing software of any kind. It could be an API endpoint, a blog, or a complex application used by millions.
Join in or share with smart people.
Let me help you!