Lock Prediction for Zero-Downtime Database Encryption
Mohamed Sami Rakha, Adam Sorrenti, Greg Stager, Walid Rjaibi, Andriy Miranskyy
https://arxiv.org/abs/2506.23985
from my link log —
ChaCha12-BLAKE3: secure, simple and fast authenticated and committing encryption for any CPU.
https://kerkour.com/chacha12-blake3
saved 2025-08-08
If you are a citizen of the EU and are concerned about government surveillance of our private chats, photographs and documents, it is important to take action before October. This tool: https://fightchatcontrol.eu/ will easily enable you to draft an email to send to your MEPs.
Specifically,
Cyber Attacks Detection, Prevention, and Source Localization in Digital Substation Communication using Hybrid Statistical-Deep Learning
Nicola Cibin, Bas Mulder, Herman Carstens, Peter Palensky, Alexandru \c{S}tefanov
https://arxiv.org/abs/2507.00522
With moving my calendar away from Google I was looking for a Caldev solution, but ...
Interesting take on CalDev and encryption on Cryptpad's github page.
No chance that that will happen encrypted.
It's waiting for an solution in the Caldev protocol. 😇
[Feature request] Possibility to have CalDAV for the Calendar · Issue #823 · cryptpad/cryptpad
Malleability-Resistant Encrypted Control System with Disturbance Compensation and Real-Time Attack Detection
Naoki Aizawa, Keita Emura, Kiminao Kogiso
https://arxiv.org/abs/2507.22693
Optimizing Indoor RIS-Aided Physical-Layer Security: A Codebook-Generation Methodology and Measurement-Based Analysis
Dimitris Kompostiotis, Dimitris Vordonis, Vassilis Paliouras, George C. Alexandropoulos
https://arxiv.org/abs/2506.22082
At the #igf2025 session on encryption and safety, they seem to be more interested in talking about tertiary issues like funding and skills shortage, but only after having the FBI share their perspectives.
Not a useful session, too one-sided, and with too little discussion on principles that actually help solve the balancing issues. 😟
E.g. principles like "Do not introduce solution…
> The encryption algorithm used for the device they examined starts with a 128-bit key, but this gets compressed to 56 bits before it encrypts traffic, making it easier to crack.
The classic approach for large key sizes.
https://arstechnica.com/secur…
SCE-NTT: A Hardware Accelerator for Number Theoretic Transform Using Superconductor Electronics
Sasan Razmkhah, Mingye Li, Zeming Cheng, Robert S. Aviles, Kyle Jackman, Joey Delport, Lieze Schindler, Wenhui Luo, Takuya Suzuki, Mehdi Kamal, Christopher L. Ayala, Coenrad J. Fourie, Nabuyuki Yoshikawa, Peter A. Beerel, Sandeep Gupta, Massoud Pedram
https://…
Forget ransomware - most firms think quantum computing is the biggest security risk to come: Quantum computers will break modern encryption sooner or later.
🔓 https://www.techradar.com/pro/security/for
I would like to see an initiative that evaluates messaging services that promise encryption and document the findings. For example, a service may claim that emails are encrypted and secure. However, if the secret keys are managed on infrastructure controlled by the service without further protection, there are limitations, and I wouldn't call it end-to-end encryption. I think it would be useful to have a neutral web page where users could lookup the security levels of services (or apps).…
A Framework of Distributed Source Encryption using Mutual Information Security Criterion and the Strong Converse Theorem
Yasutada Oohama, Bagus Santoso
https://arxiv.org/abs/2507.13294
Privacy-Preserving Drone Navigation Through Homomorphic Encryption for Collision Avoidance
Allan Luedeman, Nicholas Baum, Andrew Quijano, Kemal Akkaya
https://arxiv.org/abs/2507.14713
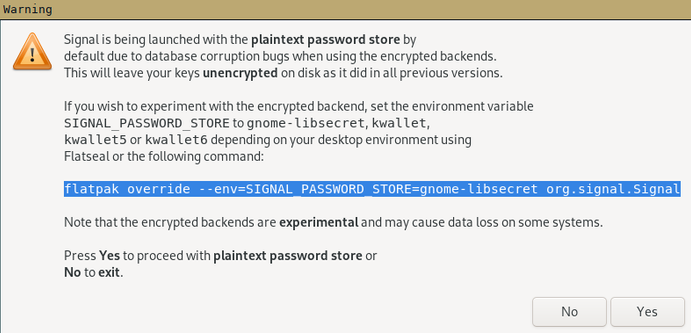
No GNOME and no KDE so no Signal Desktop for me...
It would otherwise store its password in the plain, i.e., drop encryption entirely, unless you override it to use a password store. I'm on Sway. No idea what I could do.
The EU (still) wants to scan
your private messages and photos
it’s not too late to act:
Reach out to your Representatives.
#chatcontrol #privacy #CSAM
how does it work with encryption of the links stored at your cloud? @…
This is what I always say: "It doesn't actually matter how cryptographically secure your end-to-end encryption is when 1 entity controls all ends and can instantly update them whenever they want." https://www.moparisthebest.com/against-silos-signal/
Proton launches Lumo, an AI chatbot to summarize documents, generate code, and more and says it will protect users' information via "zero-access" encryption (Emma Roth/The Verge)
https://www.theverge.com/news/711860/proton-privacy-focused-ai-chatbot
Stop reinventing email encryption for fucks sake
QuHE: Optimizing Utility-Cost in Quantum Key Distribution and Homomorphic Encryption Enabled Secure Edge Computing Networks
Liangxin Qian, Yang Li, Jun Zhao
https://arxiv.org/abs/2507.06086
Let's get the basics right for my laptop config:
- encryption during install, not jumping through hoops in partitioning
- wifi easily selected during install
- preferably non-systemd
- software not too outdated
Exactly where FreeBSD could shine, were it not for an unsupported wifi adapter 🤔
Unmasking Performance Gaps: A Comparative Study of Human Anonymization and Its Effects on Video Anomaly Detection
Sara Abdulaziz, Egor Bondarev
https://arxiv.org/abs/2507.14083

Unmasking Performance Gaps: A Comparative Study of Human Anonymization and Its Effects on Video Anomaly Detection
Advancements in deep learning have improved anomaly detection in surveillance videos, yet they raise urgent privacy concerns due to the collection of sensitive human data. In this paper, we present a comprehensive analysis of anomaly detection performance under four human anonymization techniques, including blurring, masking, encryption, and avatar replacement, applied to the UCF-Crime dataset. We evaluate four anomaly detection methods, MGFN, UR-DMU, BN-WVAD, and PEL4VAD, on the anonymized UCF…
Diving into the rabbithole of multi/hybrid cloud environments with regard to encryption, key-management, certificates, IAM etcetera. Big fun 😀
Always looking for recent and relevant literature on this subject.
#cloud #iam
HE-LRM: Encrypted Deep Learning Recommendation Models using Fully Homomorphic Encryption
Karthik Garimella, Austin Ebel, Gabrielle De Micheli, Brandon Reagen
https://arxiv.org/abs/2506.18150
I emailed all 14 Irish MEP's regarding the "Chat Control" proposal.
https://fightchatcontrol.eu/ @…
I have received a grand total of 1 response (outs…
Protect your privacy – Start now with Signal
Autocracies always implement broad surveillance methods in order to identify and punish resistance. Surveillance can take many forms including the capture of your social media posts and email, monitoring your connections to web sites, and preventing the use of private communications through encryption back-doors and other means.
Take action now to create ways to communicate privately with your family, friends and colleague…
Secure Multi-Key Homomorphic Encryption with Application to Privacy-Preserving Federated Learning
Jiahui Wu, Tiecheng Sun, Fucai Luo, Haiyan Wang, Weizhe Zhang
https://arxiv.org/abs/2506.20101
> ... but the government downplayed the danger, saying that encryption prevented access to bad actors.
[multi-decade rhetorical shrug]
https://www.theguardian.com/technology/2025/jun/22/uk-government-laptops-phones-ta…
Fight Chat Control – Protect Digital Privacy in the EU: The EU (still) wants to scan your private messages and photos.
The "Chat Control" proposal would mandate scanning of all private digital communications, including encrypted messages and photos. This threatens fundamental privacy rights and digital security for all EU citizens.
🇪🇺 https://
Microarchitecture Design and Benchmarking of Custom SHA-3 Instruction for RISC-V
Alperen Bolat, Sakir Sezer, Kieran McLaughlin, Henry Hui
https://arxiv.org/abs/2508.20653 https:…
HEIR: A Universal Compiler for Homomorphic Encryption
Asra Ali, Jaeho Choi, Bryant Gipson, Shruthi Gorantala, Jeremy Kun, Wouter Legiest, Lawrence Lim, Alexander Viand, Meron Zerihun Demissie, Hongren Zheng
https://arxiv.org/abs/2508.11095
POLARIS: Explainable Artificial Intelligence for Mitigating Power Side-Channel Leakage
Tanzim Mahfuz, Sudipta Paria, Tasneem Suha, Swarup Bhunia, Prabuddha Chakraborty
https://arxiv.org/abs/2507.22177 …
Will Cathcart says WhatsApp plans to support Apple in its legal case against the UK Home Office over weakening encryption, which may "set a dangerous precedent" (Zoe Kleinman/BBC)
https://www.bbc.com/news/articles/cgmjrn42wdwo
Toward a Lightweight, Scalable, and Parallel Secure Encryption Engine
Rasha Karakchi, Rye Stahle-Smith, Nishant Chinnasami, Tiffany Yu
https://arxiv.org/abs/2506.15070
ABC-FHE : A Resource-Efficient Accelerator Enabling Bootstrappable Parameters for Client-Side Fully Homomorphic Encryption
Sungwoong Yune, Hyojeong Lee, Adiwena Putra, Hyunjun Cho, Cuong Duong Manh, Jaeho Jeon, Joo-Young Kim
https://arxiv.org/abs/2506.08461
Adaptive Variation-Resilient Random Number Generator for Embedded Encryption
Furqan Zahoor, Ibrahim A. Albulushi, Saleh Bunaiyan, Anupam Chattopadhyay, Hesham ElSawy, Feras Al-Dirini
https://arxiv.org/abs/2507.05523
Analysis of X's new XChat shows that X can probably decrypt users' messages, as it holds users' private keys on its servers (Matthew Green/A Few Thoughts ...)
https://blog.cryptographyengineering.com/2025/06/09/a-bi…
SeDA: Secure and Efficient DNN Accelerators with Hardware/Software Synergy
Wei Xuan, Zhongrui Wang, Lang Feng, Ning Lin, Zihao Xuan, Rongliang Fu, Tsung-Yi Ho, Yuzhong Jiao, Luhong Liang
https://arxiv.org/abs/2508.18924
Characterizing the Sensitivity to Individual Bit Flips in Client-Side Operations of the CKKS Scheme
Matias Mazzanti, Augusto Vega, Esteban Mocskos
https://arxiv.org/abs/2507.20891
President Trump signs an EO scrapping or revising several Biden- and Obama-era cybersecurity programs, including for AI security and post-quantum cryptography (Eric Geller/Cybersecurity Dive)
https://www.cybersecuritydive.com/news/tru
Activate Me!: Designing Efficient Activation Functions for Privacy-Preserving Machine Learning with Fully Homomorphic Encryption
Nges Brian Njungle, Michel A. Kinsy
https://arxiv.org/abs/2508.11575
Breaking the Layer Barrier: Remodeling Private Transformer Inference with Hybrid CKKS and MPC
Tianshi Xu, Wen-jie Lu, Jiangrui Yu, Chen Yi, Chenqi Lin, Runsheng Wang, Meng Li
https://arxiv.org/abs/2508.19525
FicGCN: Unveiling the Homomorphic Encryption Efficiency from Irregular Graph Convolutional Networks
Zhaoxuan Kan, Husheng Han, Shangyi Shi, Tenghui Hua, Hang Lu, Xiaowei Li, Jianan Mu, Xing Hu
https://arxiv.org/abs/2506.10399
Versatile and Fast Location-Based Private Information Retrieval with Fully Homomorphic Encryption over the Torus
Joon Soo Yoo, Taeho Kim, Ji Won Yoon
https://arxiv.org/abs/2506.12761
A Relay-Chain-Powered Ciphertext-Policy Attribute-Based Encryption in Intelligent Transportation Systems
Aparna Singh, Geetanjali Rathee, Chaker Abdelaziz Kerrache, Mohamed Chahine Ghanem
https://arxiv.org/abs/2508.16189
SenseCrypt: Sensitivity-guided Selective Homomorphic Encryption for Joint Federated Learning in Cross-Device Scenarios
Borui Li, Li Yan, Junhao Han, Jianmin Liu, Lei Yu
https://arxiv.org/abs/2508.04100
ZAPS: A Zero-Knowledge Proof Protocol for Secure UAV Authentication with Flight Path Privacy
Shayesta Naziri, Xu Wang, Guangsheng Yu, Christy Jie Liang, Wei Ni
https://arxiv.org/abs/2508.17043
Experimental Evaluation of Post-Quantum Homomorphic Encryption for Privacy-Preserving V2X Communication
Abdullah Al Mamun, Kyle Yates, Antsa Rakotondrafara, Mashrur Chowdhury, Ryann Cartor, Shuhong Gao
https://arxiv.org/abs/2508.02461
Replaced article(s) found for cs.CR. https://arxiv.org/list/cs.CR/new
[1/2]:
- A Homomorphic Encryption Framework for Privacy-Preserving Spiking Neural Networks
Farzad Nikfam, Raffaele Casaburi, Alberto Marchisio, Maurizio Martina, Muhammad Shafique
DP2Guard: A Lightweight and Byzantine-Robust Privacy-Preserving Federated Learning Scheme for Industrial IoT
Baofu Han, Bing Li, Yining Qi, Raja Jurdak, Kaibin Huang, Chau Yuen
https://arxiv.org/abs/2507.16134
Magneto-Ionic Hardware Security Primitives: Embedding Data Protection at the Material Level
Irena Spasojevic, Federica Celegato, Alessandro Magni, Paola Tiberto, Jordi Sort
https://arxiv.org/abs/2507.14213
SECNEURON: Reliable and Flexible Abuse Control in Local LLMs via Hybrid Neuron Encryption
Zhiqiang Wang, Haohua Du, Junyang Wang, Haifeng Sun, Kaiwen Guo, Haikuo Yu, Chao Liu, Xiang-Yang Li
https://arxiv.org/abs/2506.05242
Leuvenshtein: Efficient FHE-based Edit Distance Computation with Single Bootstrap per Cell
Wouter Legiest, Jan-Pieter D'Anvers, Bojan Spasic, Nam-Luc Tran, Ingrid Verbauwhede
https://arxiv.org/abs/2508.14568