2026-02-05 11:15:19
Italy averted Russian-linked cyberattacks targeting Winter Olympics websites, foreign minister says
https://apnews.com/article/italy-winter-olympics-us-cyberattacks-security-01b6af8e64606f31836c91faa6653d12
2025-12-05 16:33:51
Degrowth cabaret comes to London (and other news)
Degrowth Cabaret! LONDON FRI 23 JANUARY 10.30am – 4.30pm Siobhan Davies Studios If you are an economist interested in performance, a performer interested in economics or simply curious in how these seemingly distinct languages can be bridged, then this session is for you! But don’t worry, you won’t need prior knowledge of economics or the arts! Joaquín Pereira (economist and dancer) invites you to a day-long lab where…
2026-02-03 21:00:04
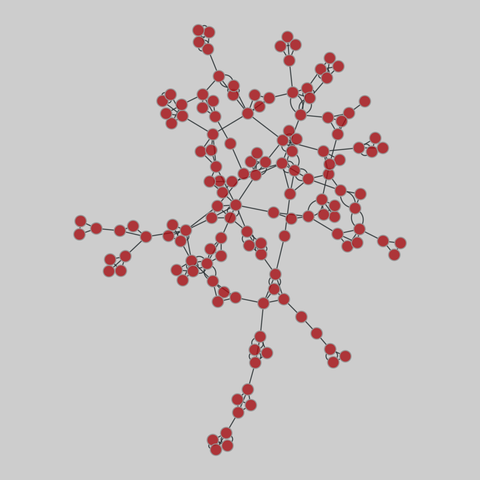
student_cooperation: Student cooperation (2012)
Network of cooperation among students in the "Computer and Network Security" course at Ben-Gurion University, in 2012. Nodes are students, and edges denote cooperation between students while doing their homework. The graph contains three types of links: Time, Computer, Partners.
This network has 185 nodes and 360 edges.
Tags: Social, Offline, Multigraph, Unweighted
2025-12-05 13:55:47
Un compañero ha preparado una encuesta sobre el nombre de nuestra cooperativa de trabajo, con una sola pregunta y una pequeña introducción con información superficial sobre el proyecto.
#cooperativismo #cooperativisme #ESS
2026-01-05 11:14:08
Greece says a radio failure that grounded flights is unlikely to be a cyberattack
https://www.wral.com/news/ap/f2ebc-greece-says-a-radio-failure-that-grounded-flights-is-unlikely-to-be-a-cyberattack/
2026-01-05 07:40:00
Taiwan: 2,6 Millionen Cyberangriffe aus China auf Infrastruktur – jeden Tag
Taiwans Nachrichtendienst hat im vergangenen Jahr im Schnitt 2,6 Millionen chinesische Cyberattacken auf die eigene kritische Infrastruktur gezählt – jeden Tag.
2026-02-04 17:00:04
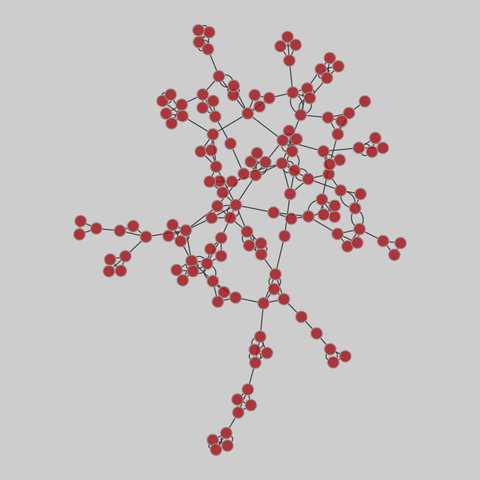
student_cooperation: Student cooperation (2012)
Network of cooperation among students in the "Computer and Network Security" course at Ben-Gurion University, in 2012. Nodes are students, and edges denote cooperation between students while doing their homework. The graph contains three types of links: Time, Computer, Partners.
This network has 185 nodes and 360 edges.
Tags: Social, Offline, Multigraph, Unweighted
2026-01-05 14:05:09
After two glorious weeks off , Metacurity is back with a holiday round-up edition of the top infosec developments you should know, including
--Substation destruction and not cyber expertise likely led to Caracas power outages,
--Denmark says Russia was behind destructive cyberattacks,
--CISA staffers suspended after organizing polygraph test of acting director,
--Chinese cyberattacks on Taiwan jumped in 2025,
--OpenAI says prompt injection attack risks are here t…
2026-01-04 04:00:04
student_cooperation: Student cooperation (2012)
Network of cooperation among students in the "Computer and Network Security" course at Ben-Gurion University, in 2012. Nodes are students, and edges denote cooperation between students while doing their homework. The graph contains three types of links: Time, Computer, Partners.
This network has 185 nodes and 360 edges.
Tags: Social, Offline, Multigraph, Unweighted
2026-02-05 14:35:08
Check out today's Metacurity for the most crucial infosec developments you should know, including
--Italy says it foiled Russian cyberattacks on foreign ministries, Olympics websites,
--NFL deploys cyber squad to secure Super Bowl,
--ShinyHunters takes credit for UPenn and Harvard attacks,
--Ransomware gangs are exploiting high-severity VMware ESXi sandbox escape vulnerability,
--Canada Computers & Electronics breach reached 1,300,
--SystemBC malwar…