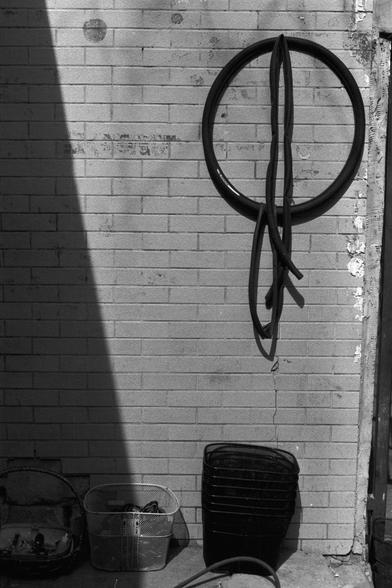2025-11-17 11:07:22
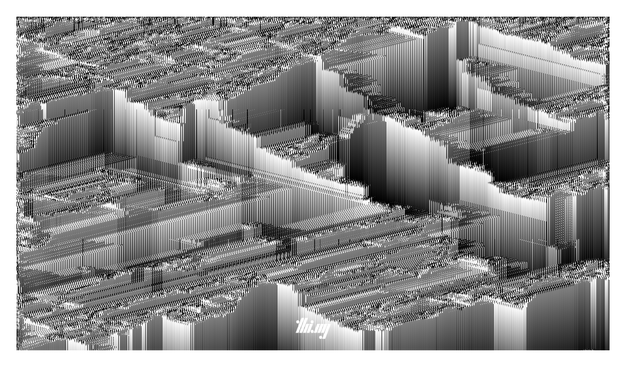
MonochromeEvolutionaryBioDigitalCellularAutomataSimulation
Unlike the recently shared[1] multi-cellular struggles, these here are some selected research stills (handpicked from tens of thousands) of only single CA configurations (aka mono-cultures) which I found interesting/promising and which were then used as raw ingredients/candidates for my infinitely evolving C-SCAPE project[2]...
Each of these cellular automata is 1.5D, meaning each pixel row is one generation, but I allowe…
2025-12-17 15:11:10
Study Finds 40% of fMRI Brain Scans Misread Neural Activity
https://ground.news/article/study-finds-40-of-fmri-brain-scans-misread-neural-activity_7aa5a7
2025-12-17 00:30:01
Metropolitana VI - Asymmetry ✅
城 VI - 非对称 ✅
📷 Pentax MX
🎞️ Ilford Pan 100
#filmphotography #Photography #blackandwhite
2025-10-17 07:04:36
And skills are remarkably simple: just a markdown file with instructions, some (Python) scripts, and optional resources.
Can’t wait for all LLM providers to adapt their new pattern!
https://www.anthropic.com/news/skills (2/2)
2025-10-14 07:40:01
Efficient Mining of Low-Utility Sequential Patterns
Jian Zhu, Zhidong Lin, Wensheng Gan, Ruichu Cai, Zhifeng Hao, Philip S. Yu
https://arxiv.org/abs/2510.10243 https://
2025-12-15 21:12:01
Got my config manager POC’d up at all levels now.
Single resource on the CLI
Idempotent shell scripts
Manifests
Globally distributed runner with patterns like rolling restarting deploys etc.
All with hierarchical data delivered via key-value store
The distributed model is using tech that. Is currently running on 7 figure node deployments.
Exciting stuff. Will make a video.
Next to make it a bit more robust etc
2025-10-15 08:37:52
Controllable Collision Scenario Generation via Collision Pattern Prediction
Pin-Lun Chen, Chi-Hsi Kung, Che-Han Chang, Wei-Chen Chiu, Yi-Ting Chen
https://arxiv.org/abs/2510.12206
2025-10-08 09:48:19
Extending ResourceLink: Patterns for Large Dataset Processing in MCP Applications
Scott Frees
https://arxiv.org/abs/2510.05968 https://arxiv.org/pdf/2510.0…
2025-10-15 07:59:31
Task-Specific Dual-Model Framework for Comprehensive Traffic Safety Video Description and Analysis
Blessing Agyei Kyem, Neema Jakisa Owor, Andrews Danyo, Joshua Kofi Asamoah, Eugene Denteh, Tanner Muturi, Anthony Dontoh, Yaw Adu-Gyamfi, Armstrong Aboah
https://arxiv.org/abs/2510.11907
2025-10-15 09:18:41
Achieving Meaningful Collaboration: Worker-centered Design of a Physical Human-Robot Collaborative Blending Task
Nicky Mol, Luka Peternel, Alessandro Ianniello, Denis Zatyagov, Auke Nachenius, Stephan Balvert, J. Micah Prendergast, Sara Muscolo, Olger Siebinga, Eva Verhoef, Deborah Forster, David A. Abbink
https://arxiv.org/abs/2510.12340