2025-10-24 11:40:26
US ‘slipping’ on cybersecurity, annual Cyberspace Solarium Commission report concludes
https://cyberscoop.com/cyberspace-solarium-commission-report-budget-workforce-cuts/
2026-01-23 06:56:20
In the Netflix/Spotify/Amazon era,
many of us access copyrighted works purely in digital form
– and that means we rarely have the chance to buy them.
Instead, we are stuck renting them,
subject to all kinds of terms and conditions.
And because the content is digital,
reselling it,
lending it,
even preserving it for your own use
inevitably requires copying.
Unfortunately, when it comes to copying digital media,
US copyright l…
2025-12-23 11:59:21
NIST, MITRE announce $20 million research effort on AI cybersecurity
https://cyberscoop.com/nist-mitre-announce-20-million-dollar-research-effort-on-ai-cybersecurity/
2025-12-24 09:18:00
Cybersicherheit: Von Ninjas, die durchs Dachfenster kommen – bei offenen Türen
Ransomware, KI-Spear-Phishing und Angst im Mittelstand: Zac Warren, Chief Security Advisor bei Tanium, über die aktuelle Lage – und Besonderheiten in der EU.
2026-01-23 13:00:05
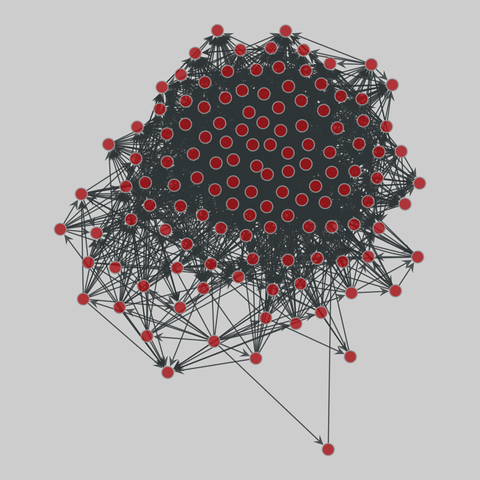
foodweb_baywet: Florida cypress wetlands food web (1998)
Networks of carbon exchanges among species in the cypress wetlands of South Florida. One network covers the wet and the other the dry season. Each node represents a taxon (similar to a species), and a directed edge indicates that one taxon uses another as food.
This network has 128 nodes and 2106 edges.
Tags: Biological, Food web, Weighted
2025-12-23 14:05:09
»Cybersicherheit — was sollten junge Menschen wissen:
Junge Internetnutzer werden oft Opfer von Betrug, Mobbing und kriminellen Übergriffen. Forscher haben jetzt einen Katalog von Fähigkeiten erstellt, die Kinder und Jugendliche für digitale Sicherheit lernen sollen.«
Alles richtig und gut so doch wann kommen die Kommerziellen online Dienstleiter diesbezüglich wirklich zur Verantwortung?
🔊
2025-12-23 11:59:20
NIST, MITRE announce $20 million research effort on AI cybersecurity
https://cyberscoop.com/nist-mitre-announce-20-million-dollar-research-effort-on-ai-cybersecurity/
2025-11-23 13:39:46
Cowboys vs. Eagles radio coverage: Station, channel, streaming to listen live to NFL Week 12 game broadcast https://www.sportingnews.com/us/nfl/news/cowboys-eagles-radio-coverage-station-channels-streaming-liste…
2025-12-24 04:25:32
40 Years Of Copyright Obstruction To Human Rights And Social Justice | Techdirt
https://www.techdirt.com/2025/12/23/40-years-of-copyright-obstruction-to-human-rights-and-social-justice/
2025-11-23 01:36:13
The Federal Communications Commission voted 2-1 along party lines on Thursday
to scrap rules that required U.S. phone and internet giants to meet certain minimum cybersecurity requirements.
The FCC’s two Trump-appointed commissioners, chairman Brendan Carr and his Republican colleague Olivia Trusty,
voted to withdraw the rules that require telecommunications carriers to “secure their networks from unlawful access or interception of communications.”
The Biden administ…