2025-11-23 16:11:28
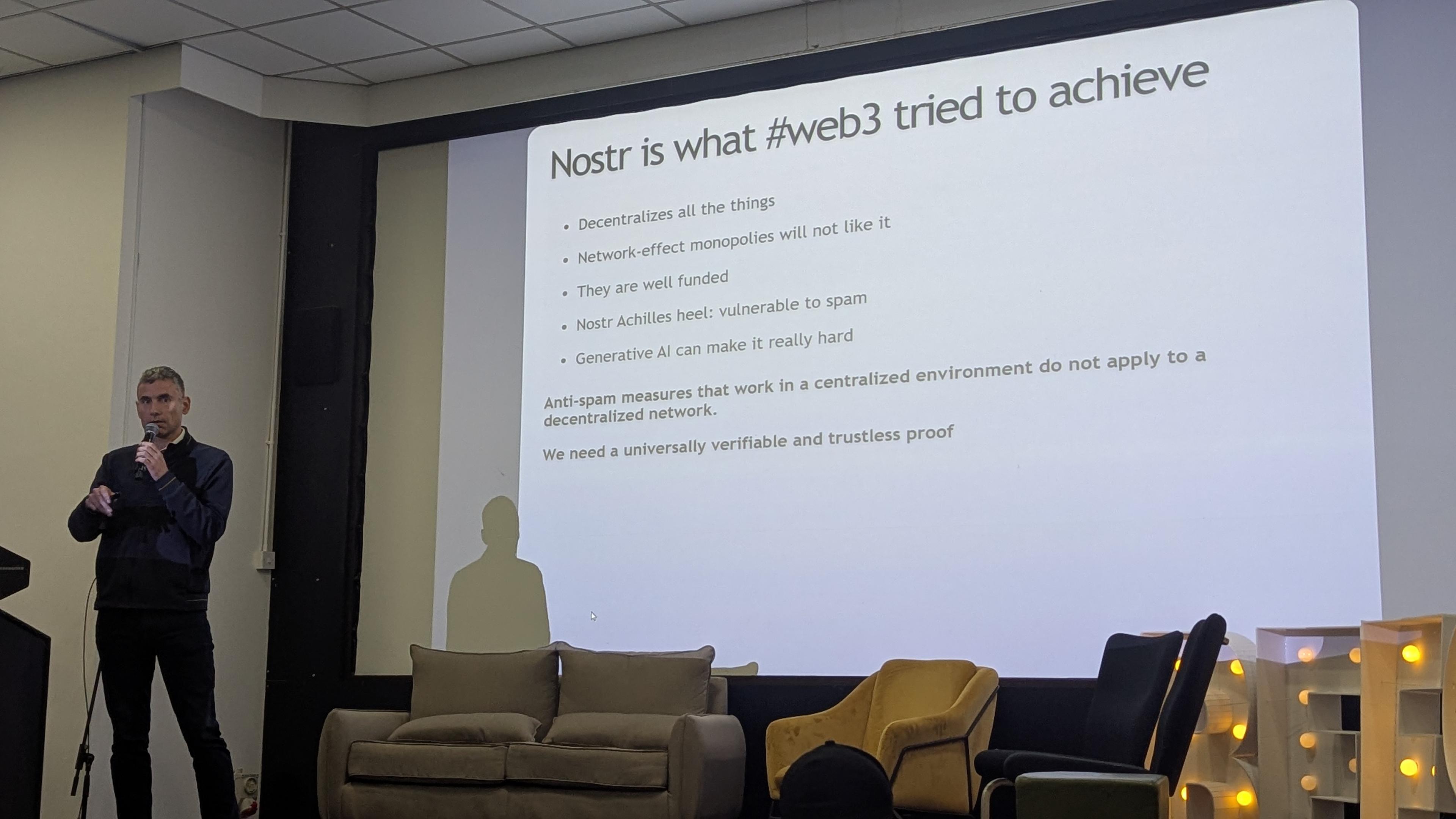
Thomas voegtlin talks about nostr spam. It's very censorship resistance means spam can't be stopped by moderators.
One way to stop spam is require proof of work before your client accepts a message. A large difficult hash.
But big hashing machines are more available to spammers than people.
Can't use likes or zaps cuz they can be faked with sybil attacks.
Instead: notaries and proveably burned satoshis.
Your public messages are classified as ham rather than spam if you burn enough money.
Nostr event types to prove it are suggested. Including burning to upvote others messages
Don't think I like deliberately burning the money, and seems to me a web of trust might work without doing that? Pay to post also peanizes there poor.
But it isn't really burned here, it's shaed out to miners to continue a subsidy when the block rewards run out. So paying miners and these notaries rather than really burning. Okay. Maybe better, but still makes messages mostly for the rich?
#bitfest #bitcoin #nostr
2025-12-18 18:42:03
from my link log —
MuseAir: A portable hashing algorithm that heavily optimized for performance and quality, incorporating structures never before implemented.
https://github.com/eternal-io/museair
saved 2025-12-18
2025-10-20 05:05:27
»The Privacy Theater of Hashed PII:
A 2020 MacBook Air can hash every North American phone number in four hours«
Good article that clearly shows that only hashing alone is not yet data safe. That's where HMAC belongs at the SHA-2 min. but also not to save passwords and the same.
🤷 https://
2025-10-10 14:42:03
from my link log —
Cuckoo hashing improves SIMD hash tables.
https://reiner.org/cuckoo-hashing
saved 2025-10-04 https://dotat.at/:/6GT24.html
2025-10-09 17:42:03
from my link log —
A new approach to analyzing Robin Hood hashing. (2014)
https://arxiv.org/abs/1401.7616
saved 2025-10-05 https://dotat.at/:/HOGQW.html…
2025-10-06 08:25:19
Probability distributions over CSS codes: two-universality, QKD hashing, collision bounds, security
Pete Rigas
https://arxiv.org/abs/2510.02402 https://arx…
2025-10-07 09:36:52
Learning-Based Hashing for ANN Search: Foundations and Early Advances
Sean Moran
https://arxiv.org/abs/2510.04127 https://arxiv.org/pdf/2510.04127
2025-10-10 09:21:29
Locality-Sensitive Hashing-Based Efficient Point Transformer for Charged Particle Reconstruction
Shitij Govil, Jack P. Rodgers, Yuan-Tang Chou, Siqi Miao, Amit Saha, Advaith Anand, Kilian Lieret, Gage DeZoort, Mia Liu, Javier Duarte, Pan Li, Shih-Chieh Hsu
https://arxiv.org/abs/2510.07594
2025-10-15 10:11:01
Hash chaining degrades security at Facebook
Thomas Rivasseau
https://arxiv.org/abs/2510.12665 https://arxiv.org/pdf/2510.12665
2025-10-25 11:42:03
from my link log —
Modern perfect hashing with tricks from computer chess.
https://blog.sesse.net/blog/tech/2025-10-23-21-23_modern_perfect_hashing.html
saved 2025-10-24