2026-02-05 20:09:03
2026-02-05 20:09:03
2025-12-06 16:07:44
#GitHub позорится как может
2026-02-06 17:46:52
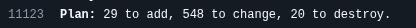
GitHub improved how its Terraform provider handles secrets. So now I shouldn't have recreations all the time. But I do have to update all of them; it only took 45 minutes to change all 500 of them:
#GitHub #Terraform
2026-02-05 07:58:35
RE: #GitHub usually posted "highlights of the new
2025-12-30 11:59:49
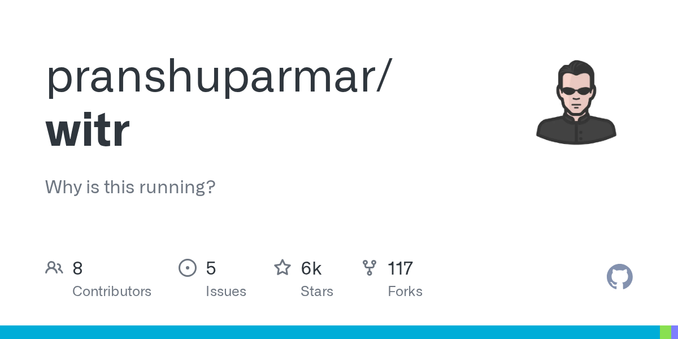
I love discovering random #GitHub projects when #HomeBrew update runs. Like this one: https://github.com/pranshuparmar/witr
2026-01-05 19:19:41
Waiting for AsahiLinux to support Thunderbolt on Apple M1. It's listed in the docs as WIP. Folks will probably get it working eventually, we just don't know when. Isn't that an annoying thing to (remember to) check on occasionally?
The AsahiLinux docs are built from markdown files in a GitHub repo. Which exposes an Atom feed of commits affecting each file. So a feed reader can occasionally check #github #atom #rss #commits
2025-12-29 16:00:04
2026-01-05 19:17:35
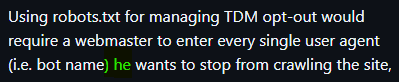
Found this unnecessary (but I'm sure unintentional) gendering in W3C's TDMRep docs repo:
Submitted an issue: 🤞
#W3C #documentation #GitHub #gendering #technology #equality #fairness
2026-02-11 09:25:31
2026-01-26 04:25:55
2026-01-30 10:19:28
So #GitHub Actions only lets me rerun all jobs, all failed jobs or a single job — not a subset of jobs. On top of that, if I rerun anything, I can't do anything until it finishes, and I can't cancel a single job without cancelling everything. Truly great UX.
So now I have to choose between either starting a few very long-running jobs one by one, and waiting for every one to finish before manually starting the next one, or starting all failed jobs, including a bunch of jobs that will rerun unnecessarily.
2026-02-08 14:45:01
To #Github Pages to całkiem ciekawe narzędzie! W ogóle nigdy nie byłem blisko z Github, ale chyba pora się z nim trochę przeprosić. Wiem, że nie jest to idealne rozwiązanie pod kątem prywatnościowym, ale chyba jednak trzeba wiedzieć przynajmniej o co w tym chodzi i jak się tego używa.
2025-12-17 08:44:04
We're about 50/50 hosted/self-hosted on CI. Been doing a bit of napkin calculations, and it seems like our total GitHub CI bill will go down by a bit after this #github change. Of course, it reduces incentives to continue migrating workloads to self hosted actions.
2026-01-13 17:11:12
2026-02-09 19:28:51
I made a #GitHub is down meme using XKCD. Have fun sharing it #developers.
2026-01-20 11:34:07
2025-12-16 21:46:56
Can't believe it's 2025 and GitHub's actions/checkout still doesn't support SHA-256. @… reported it a year ago. Apparently Microsoft is a small indie dev company with limited resources, so we should be patient with them /s
#github
2026-01-21 00:19:52
📋 #SkillSeekers - #Python tool automatically transforms documentation, #GitHub repos & PDFs into production-ready AI skills
2026-01-09 21:58:25
2025-12-18 11:14:31
2026-02-20 11:19:10
2025-12-19 14:38:09
Dear #GitHub, thank you for implementing the new, completely useless "Files changed" view that tells me to switch to the old view because it can't display more than 40 comments. Also, thanks for making your horribly useless platform the de facto standard for making reviewing anything a true misery.
2025-12-21 13:00:13
Why Most #GitHub Projects Are a Mess (And How to Fix It)
https://www.youtube.com/watch?v=gYl3moYa4iI
2026-02-10 20:21:04
RE: #blog'a na
2026-01-18 21:19:31
Around 20% of my TerraForm are GitHub Actions Secrets 🤯
#TerraForm #GitHub #Actions #Secrets
2026-02-09 09:44:20
RE: #Wordpress na
2026-02-24 16:59:40
Oh, #GitHub is empathetic to #OpenSource projects impacted by all the #AI slop. They're willing to help, right?
#Copilot even once, and of course they're not going to let people actually block this piece of shit.
#LLM #NoAI #NoLLM #hypocrisy #Microsoft
2025-12-12 21:00:57
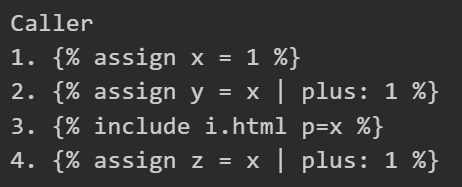
The morrow was indeed better☝️. As I suspected, there was some "Liquid in Jekyll (v3.10.0) on GH Pages" bug/feature:
Say you include `i.html` w parameter p, and this innocent line in it. Turns out this can change the type of var x in the caller. 😳
`{% assign x = include.p %} {% # x is string %}`
#webdev #technology #Jekyll #GitHub
2025-12-18 11:09:36
☸️ Hardened #Helm Charts for #Kubernetes deployments and new Hardened #MCP Servers for MongoDB, Grafana, #GitHub
2026-01-13 10:56:48
Oh, "nice". I see that #GitHub now #PGP-signs commits made via the web UI with its own key, and gives them a green "Verified" label as if *you* actually signed them.
Not that you could ever really trust labels displayed by a third party, but still.
#OpenSource #FreeSoftware
2026-01-07 04:46:42
Let's get this straight: it is entirely normal for a #OpenSource project to accumulate bug reports over time. They're not a thing to be ashamed of.
On the contrary, if you see a nontrivial project with a very small number of bug reports, it usually means one of the following:
a. you've hit a malicious fake,
b. the project is very young and it doesn't have many users (so it's likely buggy),
c. the project is actively shoving issues under the carpet.
None of that is a good sign. You don't want to use that (except for b., if you're ready to be the beta tester).
#FreeSoftware #Gentoo #GitHub #Python