Instead of relying entirely on donations and grants as before,
Mastodon announced on Friday that it will now offer paid hosting, moderation, and support services for organizations that want to join the open social web.
That network, also called the fediverse, offers a way for individuals and organizations to set up their own servers that interconnect with others that run the same protocol, ActivityPub.
ActivityPub powers a number of different software applications, includin…
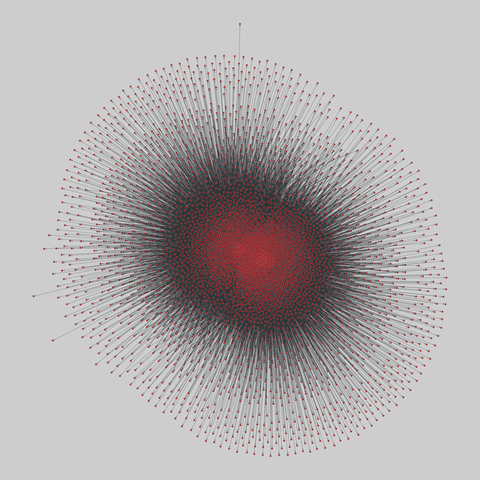
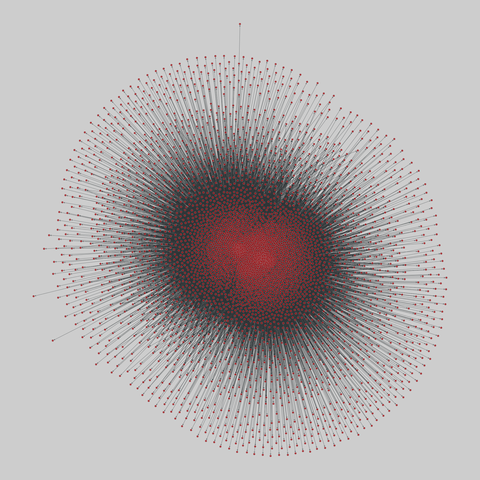
fediverse: Fediverse network (2018)
An early snapshot of the federation network among web publishers using the ActivityPub protocol. Nodes are instances, and a directed edge exists if an instance follows another instance.
This network has 4860 nodes and 484164 edges.
Tags: Social, Online, Information
https://ne…
Re-FRAME the Meeting Summarization SCOPE: Fact-Based Summarization and Personalization via Questions
Frederic Kirstein, Sonu Kumar, Terry Ruas, Bela Gipp
https://arxiv.org/abs/2509.15901
Help or Hurdle? Rethinking Model Context Protocol-Augmented Large Language Models
Wei Song, Haonan Zhong, Ziqi Ding, Jingling Xue, Yuekang Li
https://arxiv.org/abs/2508.12566 ht…
Modified security analysis of device-independent quantum key distribution with random key basis
Sawan Bhattacharyya, Turbasu Chatterjee, Pankaj Agrawal, Prasenjit Deb
https://arxiv.org/abs/2508.12938
Threat Modeling for Enhancing Security of IoT Audio Classification Devices under a Secure Protocols Framework
Sergio Benlloch-Lopez, Miquel Viel-Vazquez, Javier Naranjo-Alcazar, Jordi Grau-Haro, Pedro Zuccarello
https://arxiv.org/abs/2509.14657
Code Less to Code More: Streamlining Language Server Protocol and Type System Development for Language Families
Federico Bruzzone, Walter Cazzola, Luca Favalli
https://arxiv.org/abs/2509.15150
as_skitter: Skitter IP graph (2005)
An aggregate snapshot of the Internet Protocol (IP) graph, as measured by the traceroute tool on CAIDA's skitter infrastructure, in 2005.
This network has 1696415 nodes and 11095298 edges.
Tags: Technological, Communication, Unweighted
https://networks.skewed.de/net/as_s…
„“I think [Bluesky CEO] Jay [Graber] is great. I think the team is great,” Dorsey told Henshaw-Plath, “but the structure is what I disagree with…I want to push the energy in a different direction, which is more like Bitcoin, which is completely open and not owned by anyone from a protocol layer.“
Jack Dorsey pumps $10 million into a nonprofit focused on open-source social media | TechCrunch
Quantum State Preparation by Improved MPS Method
Chao Wang, Pengrui Zhou, Xi-Ning Zhuang, Ziwei Cui, Menghan Dou, Zhao-Yun Chen, Guo-Ping Guo
https://arxiv.org/abs/2508.12821 ht…
I’ll be attending and speaking at Fedicon, as well as being at the #CoSocialCa members meetup right after.
My working title is: Beyond Microblogging: AT Protocol for Building Unique Social Apps
https://cosocial.c…
Controlling quantum scars and engineering subharmonic responses with a two frequency drive
Pinaki Dutta, Kamal L Panigrahi, Vishwanath Shukla
https://arxiv.org/abs/2508.12809 ht…
BELT: Block Encoding of Linear Transformation on Density Matrices
Fuchuan Wei, Rundi Lu, Yuguo Shao, Junfeng Li, Jin-Peng Liu, Zhengwei Liu
https://arxiv.org/abs/2508.12858 http…
Cross-Distribution Diffusion Priors-Driven Iterative Reconstruction for Sparse-View CT
Haodong Li, Shuo Han, Haiyang Mao, Yu Shi, Changsheng Fang, Jianjia Zhang, Weiwen Wu, Hengyong Yu
https://arxiv.org/abs/2509.13576
Imaging of electrical signals in a quantum SiC microscope
A. Suhana, T. A. U. Svetikova, C. Schneider, M. Helm, A. N. Anisimov, G. V. Astakhov
https://arxiv.org/abs/2509.14888 h…
Protocol-Aware Firmware Rehosting for Effective Fuzzing of Embedded Network Stacks
Moritz Bley, Tobias Scharnowski, Simon W\"orner, Moritz Schloegel, Thorsten Holz
https://arxiv.org/abs/2509.13740
Integrated Communication and Remote Sensing in LEO Satellite Systems: Protocol, Architecture and Prototype
Yichao Xu, Xiaoming Chen, Ming Ying, Zhaoyang Zhang
https://arxiv.org/abs/2508.10317
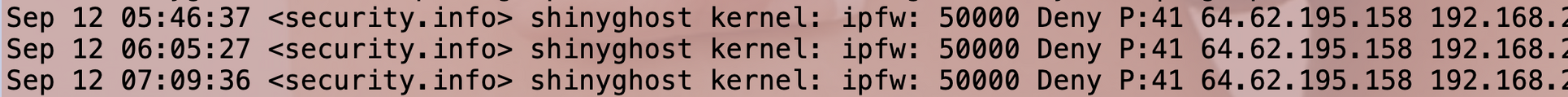
Oh #ShadowServer, now you're just being silly...
#InfoSec #Scanners
Simplified scheme for continuous-variable entanglement distillation: multicopy distillation of Gaussian entanglement without heralding Gaussian measurements
Jarom\'ir Fiur\'a\v{s}ek
https://arxiv.org/abs/2509.15065
Stuff whose job it is to log data, especially health-related data, should have a documented wire protocol. You should not be able to sell something with a 20 year old Windows installer.
Optimized Synthesis and Device Integration of Long 17-Atom-Wide Armchair Graphene Nanoribbons
Jeong Ha Hwang, Nicol\`o Bassi, Mayada Fadel, Oliver Braun, Tim Dumslaff, Carlo Pignedoli, Michael Stiefel, Roman Furrer, Hironobu Hayashi, Hiroko Yamada, Akimitsu Narita, Klaus M\"ullen, Michel Calame, Mickael L. Perrin, Roman Fasel, Pascal Ruffieux, Vincent Meunier, Gabriela Borin Barin
The superconducting grid-states qubit
Long B. Nguyen, Hyunseong Kim, Dat T. Le, Thomas Ersevim, Sai P. Chitta, Trevor Chistolini, Christian J\"unger, W. Clarke Smith, T. M. Stace, Jens Koch, David I. Santiago, Irfan Siddiqi
https://arxiv.org/abs/2509.14656
Systematic Analysis of MCP Security
Yongjian Guo, Puzhuo Liu, Wanlun Ma, Zehang Deng, Xiaogang Zhu, Peng Di, Xi Xiao, Sheng Wen
https://arxiv.org/abs/2508.12538 https://
Expediting data extraction using a large language model (LLM) and scoping review protocol: a methodological study within a complex scoping review
James Stewart-Evans, Emma Wilson, Tessa Langley, Andrew Prayle, Angela Hands, Karen Exley, Jo Leonardi-Bee
https://arxiv.org/abs/2507.06623
Minimal velocity of the travelling wave solutions in two coupled FKPP equations with the global conservation law
O. I. Baburin, I. S. Burmistrov
https://arxiv.org/abs/2509.14833
Asking for no reason whatsoever: Lots of oscilloscopes have protocol decodes for various flavors of Ethernet.
Have you ever encountered one, from any manufacturer, that is able to decode 100mbit ethernet in real time without dropping packets?
Our company sells products to test internet protocol implementations under unusual, but possible, situations. (Many fail.)
We sell worldwide, so we have to attach various code numbers to identify the type of product to the import/export (tariff/duty) government agents who make sure that things coming into their countries pay the proper fees.
Well, that list of code numbers appears to have been created in the 1970s and not updated since. So if you are selling a VHS VCR or a Fax m…
Sampled-Based Guided Quantum Walk: Non-variational quantum algorithm for combinatorial optimization
Ugo Nzongani, Dylan Laplace Mermoud, Giuseppe Di Molfetta, Andrea Simonetto
https://arxiv.org/abs/2509.15138
Fortifying the Agentic Web: A Unified Zero-Trust Architecture Against Logic-layer Threats
Ken Huang, Yasir Mehmood, Hammad Atta, Jerry Huang, Muhammad Zeeshan Baig, Sree Bhargavi Balija
https://arxiv.org/abs/2508.12259
Replaced article(s) found for cs.ET. https://arxiv.org/list/cs.ET/new
[1/1]:
- TRMAC: A Time-Reversal-based MAC Protocol for Wireless Networks within Computing Packages
Ama Bandara, Abhijit Das, Fatima Rodriguez-Galan, Eduard Alarcon, Sergi Abadal
Learning to Restore Heisenberg Limit in Noisy Quantum Sensing via Quantum Digital Twin
Hang Xu, Tailong Xiao, Jingzheng Huang, Jianping Fan, Guihua Zeng
https://arxiv.org/abs/2508.11198
Institutional Noise, Strategic Deviation, and Intertemporal Collapse: A Formal Model of Miner Behaviour under Protocol Uncertainty
Craig Steven Wright
https://arxiv.org/abs/2506.20992
Quantifying Conversation Drift in MCP via Latent Polytope
Haoran Shi, Hongwei Yao, Shuo Shao, Shaopeng Jiao, Ziqi Peng, Zhan Qin, Cong Wang
https://arxiv.org/abs/2508.06418 http…
Tunable Majorana corner states driven by superconducting phase bias in a vertical Josephson junction
Cheng-Ming Miao, Yu-Hao Wan, Ying-Tao Zhang, Qing-Feng Sun
https://arxiv.org/abs/2509.03949
IoTFuzzSentry: A Protocol Guided Mutation Based Fuzzer for Automatic Vulnerability Testing in Commercial IoT Devices
Priyanka Rushikesh Chaudhary, Rajib Ranjan Maiti
https://arxiv.org/abs/2509.09158
Scaling Artificial Intelligence for Prostate Cancer Detection on MRI towards Population-Based Screening and Primary Diagnosis in a Global, Multiethnic Population (Study Protocol)
Anindo Saha (on behalf of the PI-CAI, ProCAncer-I, COMFORT, STHLM3-MRI,PRIME consortia), Joeran S. Bosma (on behalf of the PI-CAI, ProCAncer-I, COMFORT, STHLM3-MRI,PRIME consortia), Jasper J. Twilt (on behalf of the PI-CAI, ProCAncer-I, COMFORT, STHLM3-MRI,PRIME consortia), Alexander B. C. D. Ng (on behalf of …

Scaling Artificial Intelligence for Prostate Cancer Detection on MRI towards Population-Based Screening and Primary Diagnosis in a Global, Multiethnic Population (Study Protocol)
In this intercontinental, confirmatory study, we include a retrospective cohort of 22,481 MRI examinations (21,288 patients; 46 cities in 22 countries) to train and externally validate the PI-CAI-2B model, i.e., an efficient, next-generation iteration of the state-of-the-art AI system that was developed for detecting Gleason grade group $\geq$2 prostate cancer on MRI during the PI-CAI study. Of these examinations, 20,471 cases (19,278 patients; 26 cities in 14 countries) from two EU Horizon pro…
What if each voxel were measured with a different diffusion protocol?
Santiago Coelho, Gregory Lemberskiy, Ante Zhu, Hong-Hsi Lee, Nastaren Abad, Thomas K. F. Foo, Els Fieremans, Dmitry S. Novikov
https://arxiv.org/abs/2506.22650
Generation of frequency-bin-encoded dual-rail cluster states via time-frequency multiplexing of microwave photonic qubits
Zhiling Wang, Takeaki Miyamura, Yoshiki Sunada, Keika Sunada, Jesper Ilves, Kohei Matsuura, Yasunobu Nakamura
https://arxiv.org/abs/2508.10990
Replaced article(s) found for cs.ET. https://arxiv.org/list/cs.ET/new
[1/1]:
- TRMAC: A Time-Reversal-based MAC Protocol for Wireless Networks within Computing Packages
Ama Bandara, Abhijit Das, Fatima Rodriguez-Galan, Eduard Alarcon, Sergi Abadal
Sparse Regression Codes for Secret Key Agreement: Achieving Strong Secrecy and Near-Optimal Rates for Gaussian Sources
Emmanouil M. Athanasakos, Hariprasad Manjunath
https://arxiv.org/abs/2507.20157
Symbolic Execution in Practice: A Survey of Applications in Vulnerability, Malware, Firmware, and Protocol Analysis
Joshua Bailey, Charles Nicholas
https://arxiv.org/abs/2508.06643
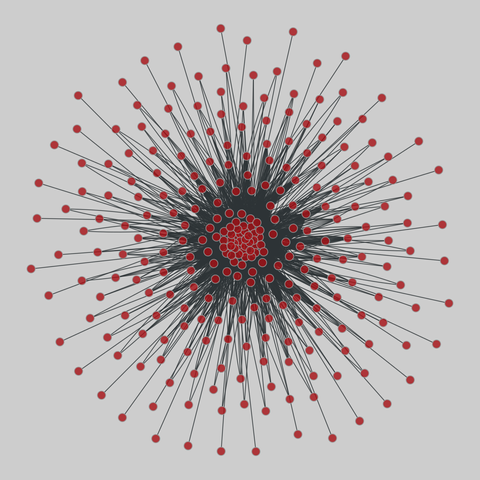
contact: Haggle human proximity network (2006)
A network of human proximities, as measured by carried wireless devices. Each node represents a person, and an edge denotes when two people were within a certain proximity of each other, as measured by a wireless protocol (Bluetooth or Wifi). The edges are timestamped.
This network has 274 nodes and 28244 edges.
Tags: Social, Offline, Unweighted, Timestamps
Improving performance of content-centric networks via decentralized coded caching for multi-level popularity and access
Azadeh Sadat Miraftab, Ahmadreza Montazerolghaem, Behrad Mahboobi
https://arxiv.org/abs/2508.01298
fediverse: Fediverse network (2018)
An early snapshot of the federation network among web publishers using the ActivityPub protocol. Nodes are instances, and a directed edge exists if an instance follows another instance.
This network has 4860 nodes and 484164 edges.
Tags: Social, Online, Information
https://ne…
TRMAC: A Time-Reversal-based MAC Protocol for Wireless Networks within Computing Packages
Ama Bandara, Abhijit Das, Fatima Rodriguez-Galan, Eduard Alarcon, Sergi Abadal
https://arxiv.org/abs/2506.19487
Further steps towards next generation of covariant energy density functionals
B. Osei, A. V. Afanasjev, A. Taninah, A. Dalbah, U. C. Perera, V. A. Dzuba, V. V. Flambaum
https://arxiv.org/abs/2507.17082
A Large-Scale Evolvable Dataset for Model Context Protocol Ecosystem and Security Analysis
Zhiwei Lin, Bonan Ruan, Jiahao Liu, Weibo Zhao
https://arxiv.org/abs/2506.23474
Indoor Positioning with Wi-Fi Location: A Survey of IEEE 802.11mc/az/bk Fine Timing Measurement Research
Katarzyna Kosek-Szott, Szymon Szott, Wojciech Ciezobka, Maksymilian Wojnar, Krzysztof Rusek, Jonathan Segev
https://arxiv.org/abs/2509.03901
From Prompt Injections to Protocol Exploits: Threats in LLM-Powered AI Agents Workflows
Mohamed Amine Ferrag, Norbert Tihanyi, Djallel Hamouda, Leandros Maglaras, Merouane Debbah
https://arxiv.org/abs/2506.23260
EGNInfoLeaker: Unveiling the Risks of Public Key Reuse and User Identity Leakage in Blockchain
Chenyu Li, Xueping Liang, Xiaorui Gong, Xiu Zhang
https://arxiv.org/abs/2507.01635
Is Crunching Public Data the Right Approach to Detect BGP Hijacks?
Alessandro Giaconia, Muoi Tran, Laurent Vanbever, Stefano Vissicchio
https://arxiv.org/abs/2507.20434 https://…