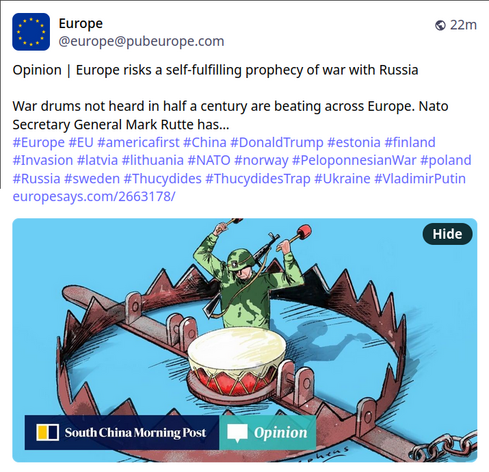
Thank you all for 3,000 followers on here! Here’s a photo of Danny to celebrate the occasion ☺️
3 years into being part of Mastodon, I continue to be impressed with how wonderful the people here are and how much this social network actually FEELS social. People replying to one another, having conversations, learning things, sharing moments of joy, making friends.
Mastodon brought my business clients, helped me gain confidence in my own voice, freed me from dependence on big tech and algorithms, rekindled my interests, introduced me to incredible people and projects, and served as a source of hope in humanity in the times when cynicism and nihilism felt all but inevitable.
I love our little corner of the internet, and am so glad that it’s still here despite everyone who professed it was doomed to fade into irrelevance.
Thank you to everyone reading these words for being here on the Fedi. The world is a little better thanks to your choice to support an independent web.