2025-12-13 10:10:41
10 Years of Let's Encrypt #Certificates
https://letsencrypt.org/2025/12/09/10-years
Mindblowing statistics of this extremely important project, delivering
2026-02-12 08:38:21
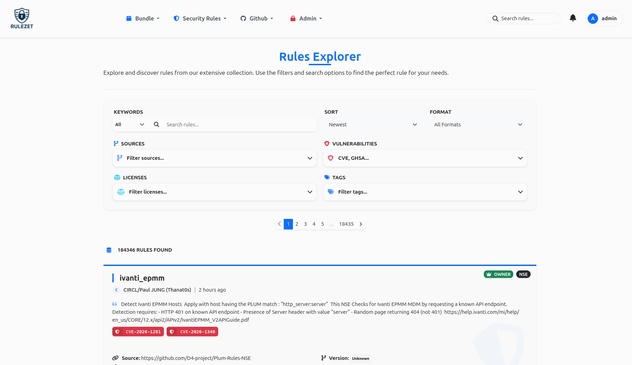
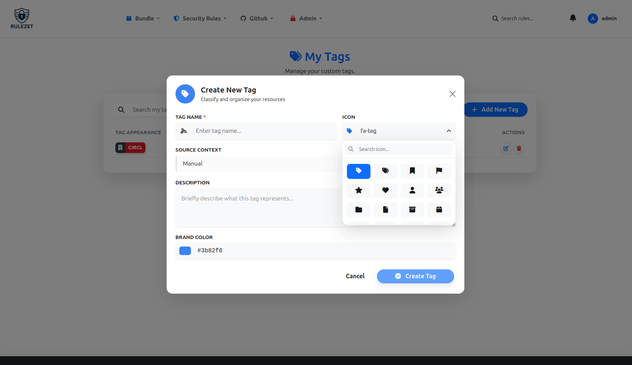
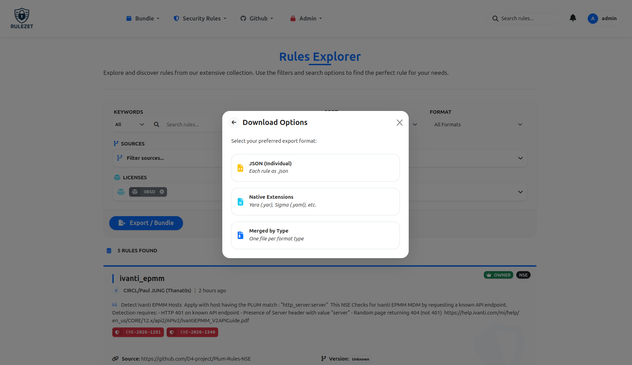
Rulezet (The detection rule management) v1.4.0 released — Taxonomy, Precision, and Advanced Discovery
Version 1.4.0 is a milestone update that transforms how intelligence is categorized and retrieved within Rulezet. By placing Tags and Taxonomies at the heart of the ecosystem, this release empowers users with granular control over their data. From private custom tagging to a revolutionary filtering engine, v1.4.0 ensures that finding the right rule is no longer a search—it’s a precisio…
2026-02-12 22:55:51
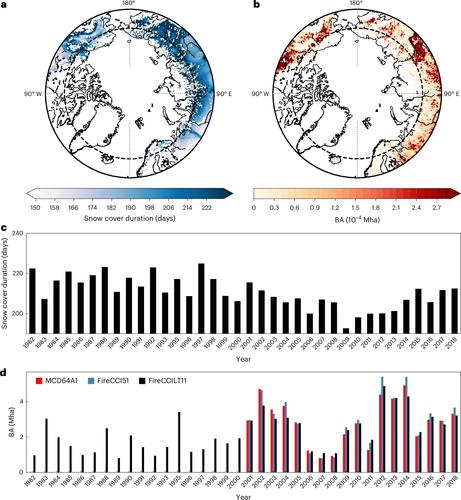
Forests are changing fast and scientists are deeply concerned #environment
2026-01-13 17:11:12
2026-01-13 18:01:14
DOJ's top civil rights prosecutors depart as office is cut out of key probes (Perry Stein/Washington Post)
https://www.washingtonpost.com/national-security/2026/01/13/justice-department-civil-rights-resignations/?pwapi_token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyZWFzb24iOiJnaWZ0IiwibmJmIjoxNzY4MjgwNDAwLCJpc3MiOiJzdWJzY3JpcHRpb25zIiwiZXhwIjoxNzY5NjYyNzk5LCJpYXQiOjE3NjgyODA0MDAsImp0aSI6IjExZDg5ZGQxLTljMDItNGM1MC05MDg5LTFkZjcyMDc2MjQ4MCIsInVybCI6Imh0dHBzOi8vd3d3Lndhc2hpbmd0b25wb3N0LmNvbS9uYXRpb25hbC1zZWN1cml0eS8yMDI2LzAxLzEzL2p1c3RpY2UtZGVwYXJ0bWVudC1jaXZpbC1yaWdodHMtcmVzaWduYXRpb25zLyJ9.I2JIbp1zVNnNmX1whIYkF0od4QhnaL85Hng0g3SkjK8&itid=gfta
http://www.memeorandum.com/260113/p87#a260113p87
2025-12-12 06:57:04
2025-12-12 06:32:54
2026-01-12 08:24:45
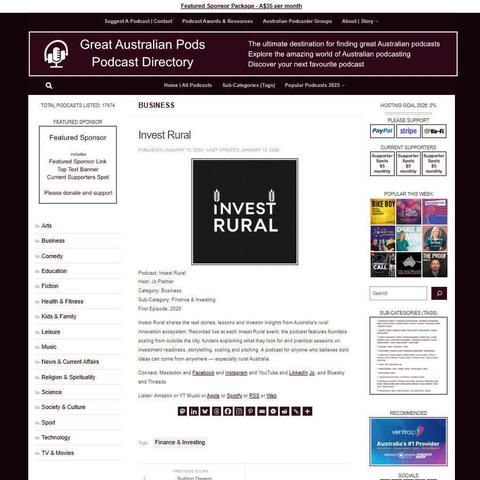
Invest Rural
Shares the real stories, lessons and investor insights from Australia's rural innovation ecosystem...
Great Australian Pods Podcast Directory: https://www.greataustralianpods.com/invest-rural/
2026-01-11 19:56:43
Frequent Arctic wildfires could cut snow cover by 18 days, impacting global climate and ecology #Arctic
2025-12-12 09:25:57
🦋 librepods: AirPods liberated from Apple's ecosystem
#airpods