A three judge panel of the 9th Circuit had ruled that the Trump Admin. likely has the authority to send the military to Portland under 10 U.S.C. § 12406(3)
"when the President is unable with the regular forces to execute the laws of the United States”
Having the full bench take it up seems encouraging!
https://
RE: https://mastodon.energy/@Sustainable2050/115957799005351310
I would never have suspected that the US of would execute a restrained wounded protester and that the shooter could get away with it.
(I hope 'get away for now and get prosecuted later', but I don't know...)
✅ order extra HDD for a cold backup
Todo: best way to execute it
My brain seems to have two modes:
1. time-unaware, that slightly chaotic relaxed flow state where I just do the next thing that feels right
2. time-aware, which is always a bit tense and stressful because I need to force myself to keep to a calendar, and execute tasks in specific times.
Little JavaScript tip:
You know you can comment out code to quickly disable it:
```js
/*
console.log(‘I won’t run’)
*/
```
But did you know you can also use a labelled block with a break statement to do the same thing in a more flexible manner?
```js
disable: {
break disable
console.log(‘I wont’t run’)
}
```
Then, you can quickly the move the `break disable` to different lines to execute different bits of code wit…
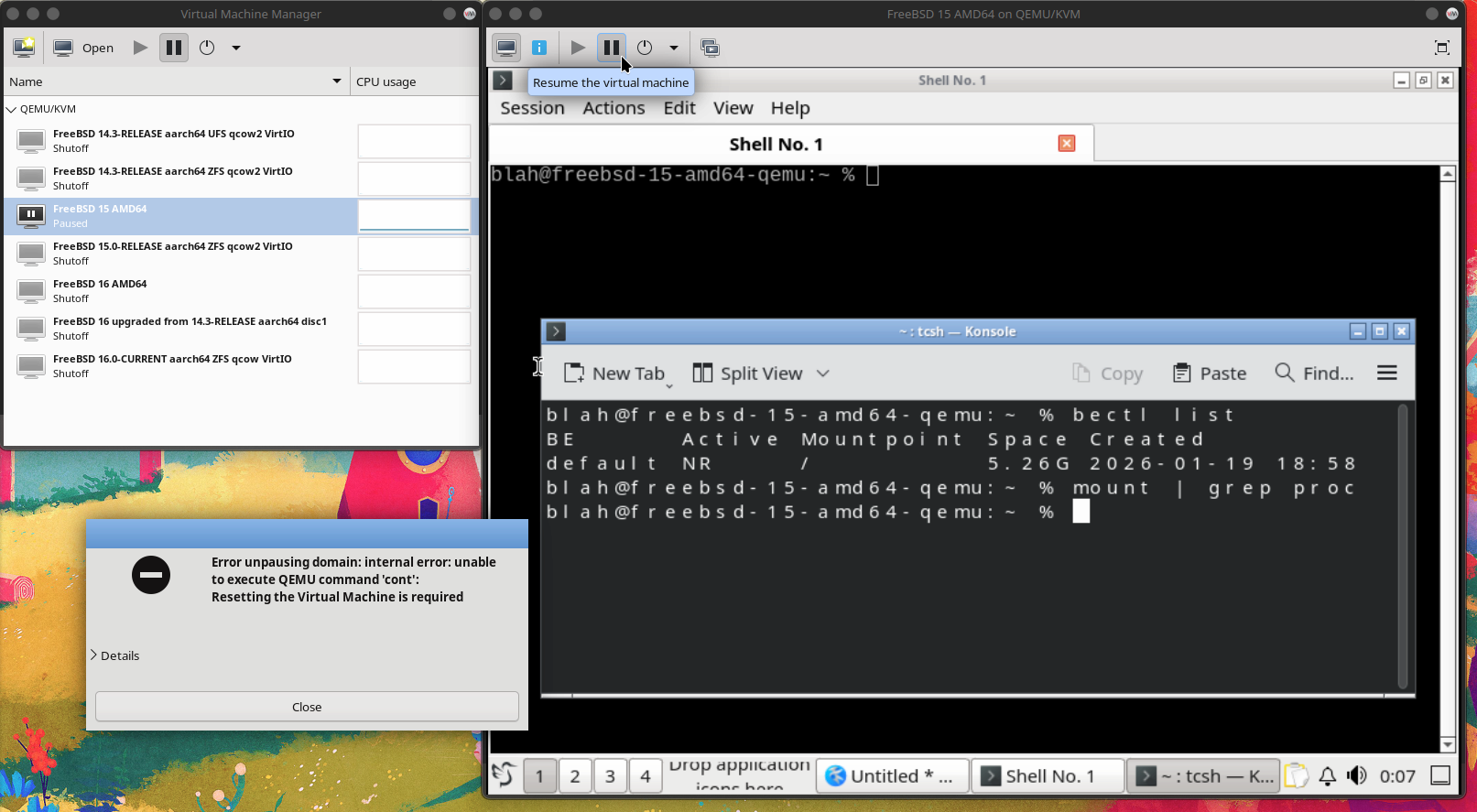
Unable to resume a paused machine in QEMU.
Is this expected, after concurrent use of VirtualBox?
<https://pastebin.com/raw/rhAGGbMt>
libvirt.libvirtError: internal error: unable to execute QEMU command 'cont': Resetting the Virtual Machine is required
Preceding the erro…
Manus says it crossed $100M ARR eight months after launch and is growing at 20% MoM since Manus 1.5's release; its total revenue run rate is now over $125M (Jake Rudnitsky/Bloomberg)
https://www.bloomberg.com/news/articles/20
#Iran closes airspace to all flights as foreign minister denies it plans to execute protesters
German airline #Lufthansa has said it will bypass Iranian and Iraqi airspace “until further notice”, Agence France-Presse is reporting.
The group, which includes Austrian, Brussels Airlines, Discover, Eurowings, Swis…
from my link log —
Execute-only pages vs PAN (privileged access never) on arm64.
https://siguza.github.io/PAN/
saved 2020-01-07 https://dotat.at/:/CBAC3.h…
=== ALL USERS PLEASE NOTE ========================
JCL support as alternative to system menu.
In our continuing effort to support languages other than LISP on the CADDR,
we have developed an OS/360-compatible JCL. This can be used as an
alternative to the standard system menu. Type System J to get to a JCL
interactive read-execute-diagnose loop window. [Note that for 360
compatibility, all input lines are truncated to 80 characters.] This
window als…
The U.S. invaded another country and potentially destabilized an entire continent (maybe up to three) to execute an arrest warrant based on U.S. laws that have no jurisdiction there.
If AI chatbot companies truly had what they claim they have (arbitrary scaling human-level intelligence)—they would use it exclusively themselves, prompting it to come up with schemes to make money and execute them.
In reality these companies all lose money (in historically unprecedented amounts), to fuel a drug dealer-like approach by giving it away for free and hoping enough people get addicted to sycophantic chatbots; with the goal to charge exorbitant fees for it in the future.
Coast Guard allows Swastikas, nooses, and confederate flags.
The U.S. military accidentally conducts incursion into Mexico.
Senator Slotkin joins me to talk about intelligence agencies conducting operations on American soil
and to respond to Trump's calls to execute her.
https://
Imagine a threat intelligence report that concludes, ‘The target is three hops away, therefore it is the correct one.’ This is the method the Pentagon reportedly uses today: not only to identify targets, but also to justify and execute strikes.
🔗 https://theweek.com/politics/pentagon-
Word of the day: AI-washing
"Where management wants to cut labor costs a la Amazon, shift to cheaper contract labor a la Klarna, or execute layoffs for ideological reasons, a la DOGE, “AI” is an extremely potent justification. Some business professors and analysts have taken to calling this practice “AI-washing.””
From Brian Merchants excellent Blood in the Machine newsletter/substack.
Trump: Execute drug dealers, free kingpins
Longtime Trump associate and right-wing operative Roger Stone personally lobbied for Hernandez’s release of Juan Orlando Hernandez, who had just started serving a 45-year federal prison sentence for helping to traffic hundreds of tons of cocaine into the United States
— free of charge, Stone claims.
Meanwhile, former Trump campaign manager Brad Parscale has been working for the campaign of Nasry Asfura, the right-wing candidate f…
A Death Row Inmate Was Released on Bail
BAfter His Conviction Was Overturned.
Louisiana Still Wants to Execute Him.
Months after a judge tossed out his 1998 murder conviction,
Jimmie Duncan is free on bail.
But prosecutors have asked the Louisiana Supreme Court to reinstate the death penalty for Duncan,
even as the victim’s mother has come to support his release
Selling Privacy in Blockchain Transactions
Georgios Chionas, Olga Gorelkina, Piotr Krysta, Rida Laraki
https://arxiv.org/abs/2512.08096 https://arxiv.org/pdf/2512.08096 https://arxiv.org/html/2512.08096
arXiv:2512.08096v1 Announce Type: new
Abstract: We study methods to enhance privacy in blockchain transactions from an economic angle. We consider mechanisms for privacy-aware users whose utility depends not only on the outcome of the mechanism but also negatively on the exposure of their economic preferences. Specifically, we study two auction-theoretic settings with privacy-aware users. First, we analyze an order flow auction, where a user auctions off to specialized agents, called searchers, the right to execute her transaction while maintaining a degree of privacy. We examine how the degree of privacy affects the revenue of the auction and, broadly, the net utility of the privacy-aware user. In this new setting, we describe the optimal auction, which is a sealed-bid auction. Subsequently, we analyze a variant of a Dutch auction in which the user gradually decreases the price and the degree of privacy until the transaction is sold. We compare the revenue of this auction to that of the optimal one as a function of the number of communication rounds. Then, we introduce a two-sided market - a privacy marketplace - with multiple users selling their transactions under their privacy preferences to multiple searchers. We propose a posted-price mechanism for the two-sided market that guarantees constant approximation of the optimal social welfare while maintaining incentive compatibility (from both sides of the market) and budget balance. This work builds on the emerging line of research that attempts to improve the performance of economic mechanisms by appending cryptographic primitives to them.
toXiv_bot_toot
Donald Trump says he has been assured the killing of Iranian protesters has been halted,
while adding he will “watch it and see” about threatened US military action.
The president said at the White House that “very important sources on the other side” had also now assured him that Iranian executions would not go ahead, Agence France-Presse is reporting.
“They’ve said the killing has stopped and the executions won’t take place,” Trump said.
There were supposed to be a …
Iran extends airspace closure
Iran further extended an order closing its airspace to commercial aircraft without explanation early on Thursday.
A notice to pilots said the closure was estimated to last until 7.30am local time, the AP is reporting.
A previous order had closed the airspace for just over two hours.
The Iranian government offered no explanation of the decision to shut its airspace amid the tensions with Washington over Tehran’s protest crackdown.
For years, Donald Trump has fantasized about lawlessly killing drug dealers
In his second term, he’s made the fantasy a reality,
killing putative "drug dealers" in a likely illegal airstrike campaign on vessels in international waters.
Yet at the same time, Trump last week pardoned former Honduran President Juan Orlando Hernandez,
who had just started serving a 45-year federal prison sentence for helping to traffic
💥 hundreds of tons of cocaine💥 into t…