2025-11-19 14:09:00
KI-Update kompakt: Gemini 3, Mathematik-Modell, Milchstraße, KI-Blase
Das "KI-Update" liefert drei mal pro Woche eine Zusammenfassung der wichtigsten KI-Entwicklungen.
https://www.
2025-10-21 13:08:03
2025-10-20 01:44:56
When you claim the unilateral authority to pay troops out of money specifically allocated for other purposes,
surprising things happen in the law.
https://bsky.app/profile/ridleydm.bsky.social/post/3m3ljygk7qs24
2025-12-21 20:37:01
a human: "I want to put a cat that is physically able to kill me in approximately ten milliseconds in my home and share my life with it"
(One day passes)
same human: "I am going to annoy the animal that can split my spinal cord in two on purpose because I am bored"
never gets old https://www.youtube.com/sh…
2025-11-22 00:15:25
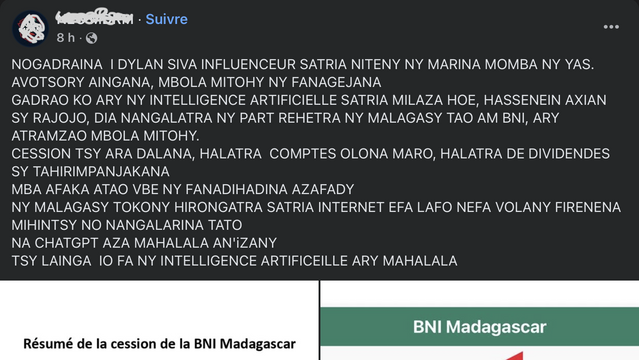
Sendra nahita an'ity post Facebook ity aho…
LOL be kosa ry ireto â…
Tsy mitsahatra ny miteny eto aho hoe : aza matoky ChatGPT fa tsy mahazo resaka io fa miezaka manodikodina fotsiny izay hitakitany any, tahaka ny ankizy ampianarina manoratra dia mitady soratra azo adika mba hizestiavana manoloana an’i Nenitoa…
#ChatGPT
2025-09-22 12:07:37
2025-11-21 17:20:15
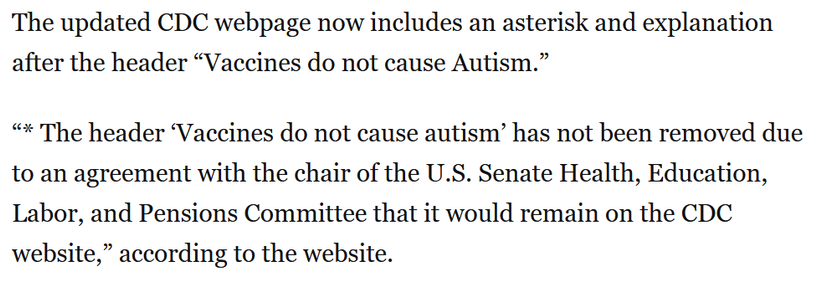
It’s fitting RFK is maliciously conforming to a promise he made to a Republican senator / doctor in order to get his confirmation vote.
https://archive.is/aEILc#selection-589.0-595.236:~:text=The updated,website,-.
Liar’s gonna lie and t…
2025-11-17 10:36:00
Dank KI: Erstmals komplette Milchstraße inklusive aller Sterne simuliert
Unsere Milchstraße besteht aus 100 Milliarden Sternen. Bisher konnten Simulationen sie nicht einzeln einbeziehen – dank KI ist das jetzt erstmals gelungen.
2025-10-19 22:54:49
Folks demanding political / ideological purity
fail to see that this is no longer a movement belonging to the left / liberals.
This is an opposition against fascism.
By definition it must be big tent.
Failure to grasp this: see divided oppositions in Eastern Europe as your failed examples.
https://
2025-10-20 11:00:00


![[fr] Copie d’écran d’un « Résumé de la cession de la BNI Madagascar » généré par ChatGPT](https://mastodon.mg/system/media_attachments/files/115/590/465/144/587/839/small/5c7bc85eb55e6518.png)