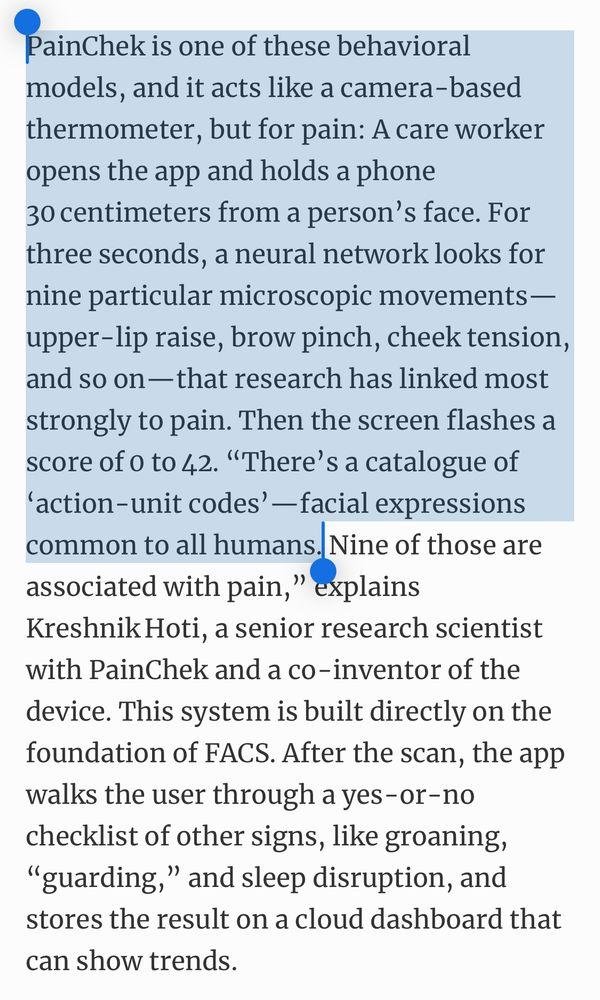
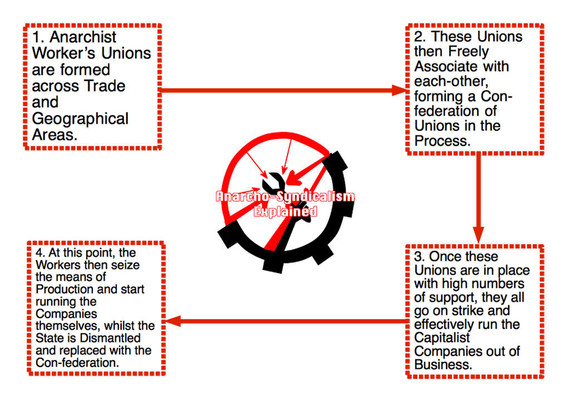
2025-10-19 01:42:49
2025-10-19 01:42:49
2025-12-17 00:15:50
Makary denies plans for COVID-19 black box warning (Joseph Choi/The Hill)
https://thehill.com/policy/healthcare/5651857-fda-denies-black-box-warning-covid19/
http://www.memeorandum.com/251216/p134#a251216p134
2025-12-17 10:06:51
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-10-16 14:32:47
"In a world beset by war, genocide, systemic discrimination, and climate catastrophe, we need good news. Donyelle McCray offers the opportunity to hear and see the embodiment of good news emanating from marginalized voices—especially Black women, laypeople, artists, and activists."
From the Christian Century review of the new book by YDS professor Donyelle McCray, "Is it a Sermon?"
2025-10-15 19:12:23
2025-10-14 09:06:28
Latent-Feature-Informed Neural ODE Modeling for Lightweight Stability Evaluation of Black-box Grid-Tied Inverters
Jialin Zheng, Zhong Liu, Xiaonan Lu
https://arxiv.org/abs/2510.09826
2025-10-16 17:36:12
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-11-09 19:44:14
I actually only needed some small light in order to be able to identify things in the dark box in low light conditions.
Somehow, that escalated quickly and turned into some #Christmas thing. 😎
Just two 7€ xmas LED sets with a 3xAA battery pack each.
#muli
2025-10-14 10:41:58
A Black-Box Debiasing Framework for Conditional Sampling
Han Cui, Jingbo Liu
https://arxiv.org/abs/2510.11071 https://arxiv.org/pdf/2510.11071
2025-10-13 10:30:00
Verifying Chain-of-Thought Reasoning via Its Computational Graph
Zheng Zhao, Yeskendir Koishekenov, Xianjun Yang, Naila Murray, Nicola Cancedda
https://arxiv.org/abs/2510.09312 …
2025-10-06 10:24:09
ZeroShotOpt: Towards Zero-Shot Pretrained Models for Efficient Black-Box Optimization
Jamison Meindl, Yunsheng Tian, Tony Cui, Veronika Thost, Zhang-Wei Hong, Johannes D\"urholt, Jie Chen, Wojciech Matusik, Mina Konakovi\'c Lukovi\'c
https://arxiv.org/abs/2510.03051
2025-10-10 09:53:39
Accelerated Aggregated D-Optimal Designs for Estimating Main Effects in Black-Box Models
Chih-Yu Chang, Ming-Chung Chang
https://arxiv.org/abs/2510.08465 https://
2025-10-09 09:21:21
Reading Between the Lines: Towards Reliable Black-box LLM Fingerprinting via Zeroth-order Gradient Estimation
Shuo Shao, Yiming Li, Hongwei Yao, Yifei Chen, Yuchen Yang, Zhan Qin
https://arxiv.org/abs/2510.06605
2025-10-02 10:50:31
ZQBA: Zero Query Black-box Adversarial Attack
Joana C. Costa, Tiago Roxo, Hugo Proen\c{c}a, Pedro R. M. In\'acio
https://arxiv.org/abs/2510.00769 https://
2025-11-09 00:30:38
Moody Urbanity - Relations 👥
情绪化城市 - 关系 👥
📷 Minolta Hi-Matic AF
🎞️ Shanghai GP3 400 Pan
#filmphotography #Photography #blackandwhite
2025-10-13 14:52:21
Proton: an incredible feat of software engineering; a Rube Goldberg machine that brought Windows gaming to Linux seemingly overnight after decades of Windows domination.
Copilot: a black box inflationary doodad riding the Nvidia wings after the crypto bubble; airplanes not falling from sky only because traffic control probably doesn't have it installed on critical hardware.
2025-10-10 19:12:22
Finished “I’m Starting to Worry About This Black Box of Doom” by Jason Pargin. A Lyft driver is asked by a woman to drive her and a mysterious box across the country for $200k. The rules are that he cannot look inside, nor ask about the contents. Everything comes undone along the way in a mostly fun, pulpy thriller kind of way.
Some dark satire about anxiety, the web, social media, public discourse, incels, etc.
3.5/5 stars, rounded up to 4/5 ⭐️⭐️⭐️⭐️
2025-11-09 16:24:37
2025-11-15 21:34:45
2025-12-10 18:42:01
from my link log —
Black-box concurrent data structures for NUMA architectures.
https://cs.brown.edu/~irina/papers/asplos2017-final.pdf
saved 2023-09-09
2025-09-26 10:06:51
Limits to black-box amplification in QMA
Scott Aaronson, Freek Witteveen
https://arxiv.org/abs/2509.21131 https://arxiv.org/pdf/2509.21131
2025-10-23 19:48:14
Rob Jetten of een debat waar ik geen zij ij heb.. Sja .... Dan maar naar de buren.
Polizeiruf 110: Black Box - hier anschauen
https://www.ardmediathek.de/video/polizeiruf-110/black-box/mdr/Y3JpZDovL21kci5kZS9zZW5kdW5nLzI4MjA0MC80MDgwODEtMzg4NDk4
2025-10-01 10:59:07
Black-box Context-free Grammar Inference for Readable & Natural Grammars
Mohammad Rifat Arefin, Shanto Rahman, Christoph Csallner
https://arxiv.org/abs/2509.26616 https://…
2025-12-14 09:41:46
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-10-14 10:33:48
ProGress: Structured Music Generation via Graph Diffusion and Hierarchical Music Analysis
Stephen Ni-Hahn, Chao P\'eter Yang, Mingchen Ma, Cynthia Rudin, Simon Mak, Yue Jiang
https://arxiv.org/abs/2510.10249
2025-11-04 20:35:59
When did we move from a OKish "out of the box"-experience to a even worse "out of the black-box"-experience…
2025-10-03 08:59:11
MetaSynth: Multi-Agent Metadata Generation from Implicit Feedback in Black-Box Systems
Shreeranjani Srirangamsridharan, Ali Abavisani, Reza Yousefi Maragheh, Ramin Giahi, Kai Zhao, Jason Cho, Sushant Kumar
https://arxiv.org/abs/2510.01523
2025-10-15 10:38:21
Probing Latent Knowledge Conflict for Faithful Retrieval-Augmented Generation
Linfeng Gao, Baolong Bi, Zheng Yuan, Le Wang, Zerui Chen, Zhimin Wei, Shenghua Liu, Qinggang Zhang, Jinsong Su
https://arxiv.org/abs/2510.12460
2025-11-28 00:59:34
🇺🇦 #NowPlaying on KEXP's #DriveTime
Black Box:
🎵 Everybody Everybody
#BlackBox
https://edit-mix.bandcamp.com/track/black-box-everybody-everybody-hot-mix-118-bpm
https://open.spotify.com/track/6wBMTv8yTiNh50fqTkT0JC
2025-10-07 10:32:22
AgentTypo: Adaptive Typographic Prompt Injection Attacks against Black-box Multimodal Agents
Yanjie Li, Yiming Cao, Dong Wang, Bin Xiao
https://arxiv.org/abs/2510.04257 https://…
2025-10-10 10:26:59
AutoQual: An LLM Agent for Automated Discovery of Interpretable Features for Review Quality Assessment
Xiaochong Lan, Jie Feng, Yinxing Liu, Xinlei Shi, Yong Li
https://arxiv.org/abs/2510.08081
2025-09-26 09:06:41
Machine Learning Powered Feasible Path Framework with Adaptive Sampling for Black-box Optimization
Zixuan Zhang, Xiaowei Song, Jiaming Li, Yujiao Zeng, Yaling Nie, Min Zhu, Dongyun Lu, Yibo Zhang, Xin Xiao, Jie Li
https://arxiv.org/abs/2509.21077
2025-10-13 10:24:30
Hallucination Filtering in Radiology Vision-Language Models Using Discrete Semantic Entropy
Patrick Wienholt, Sophie Caselitz, Robert Siepmann, Philipp Bruners, Keno Bressem, Christiane Kuhl, Jakob Nikolas Kather, Sven Nebelung, Daniel Truhn
https://arxiv.org/abs/2510.09256
2025-12-13 13:06:43
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-09-30 09:34:51
Boundary on the Table: Efficient Black-Box Decision-Based Attacks for Structured Data
Roie Kazoom, Yuval Ratzabi, Etamar Rothstein, Ofer Hadar
https://arxiv.org/abs/2509.22850 h…
2025-11-28 19:10:47
free waves audio magma stressbox ig https://www.waves.com/black-friday-2025/free-plugin
2025-10-06 10:19:29
Leave No TRACE: Black-box Detection of Copyrighted Dataset Usage in Large Language Models via Watermarking
Jingqi Zhang, Ruibo Chen, Yingqing Yang, Peihua Mai, Heng Huang, Yan Pang
https://arxiv.org/abs/2510.02962
2025-09-27 01:50:00
It's THAT time of year again - @lifting_the_lid_festival has opened up ticket sales for the fifth annual event this November!
Information, networking, entertainment, food for thought, discussions and all the best of deathly content is yours for a remarkably low price. A full three days of excitement awaits you - get your ticket here: htt…
2025-11-02 14:57:02
Nick Drake - "The Making of Five Leaves Left" (2025)
My pre-order for this got canceled because there's a fucking moron in the White House, but I managed to snag another copy for twice the price. Would that that was the only negative impact of Drumpf.
#NowPlaying #NickDrake
2025-10-02 06:36:00
Interactive semantic segmentation for phosphene vision neuroprosthetics https://arxiv.org/abs/2509.19957 "findings demonstrate the value of user feedback and the potential of gaze-guided semantic segmentation to enhance neuroprosthetic vision";
2025-11-14 13:30:10
Replaced article(s) found for stat.ML. https://arxiv.org/list/stat.ML/new
[1/1]:
- Provably Scalable Black-Box Variational Inference with Structured Variational Families
Joohwan Ko, Kyurae Kim, Woo Chang Kim, Jacob R. Gardner
2025-10-14 12:13:08
RAG-Pull: Imperceptible Attacks on RAG Systems for Code Generation
Vasilije Stambolic, Aritra Dhar, Lukas Cavigelli
https://arxiv.org/abs/2510.11195 https://
2025-11-28 05:22:26
We don't allow cats on our dinner table, and they full well know that (their punishment when caught is corporal cuddling).
While I was out of the house just now and my wife asleep, the 13yo took this picture.
Oh yeah, my wife's laptop often seems to mysterious crash overnight..
#CatsOfMastodon
2025-12-01 07:12:09
 @axbom@axbom.me
@axbom@axbom.me2025-09-22 20:22:38
2025-10-13 09:25:10
Reliability Sensitivity with Response Gradient
Siu-Kui Au, Zi-Jun Cao
https://arxiv.org/abs/2510.09315 https://arxiv.org/pdf/2510.09315
2025-10-09 09:01:31
An Integral Equation Method for Linear Two-Point Boundary Value Systems
Tianze Zhang, Yixuan Ma, Jun Wang
https://arxiv.org/abs/2510.06678 https://arxiv.or…
2025-12-10 08:38:00
Manifolds and Modules: How Function Develops in a Neural Foundation Model
Johannes Bertram, Luciano Dyballa, T. Anderson Keller, Savik Kinger, Steven W. Zucker
https://arxiv.org/abs/2512.07869 https://arxiv.org/pdf/2512.07869 https://arxiv.org/html/2512.07869
arXiv:2512.07869v1 Announce Type: new
Abstract: Foundation models have shown remarkable success in fitting biological visual systems; however, their black-box nature inherently limits their utility for under- standing brain function. Here, we peek inside a SOTA foundation model of neural activity (Wang et al., 2025) as a physiologist might, characterizing each 'neuron' based on its temporal response properties to parametric stimuli. We analyze how different stimuli are represented in neural activity space by building decoding man- ifolds, and we analyze how different neurons are represented in stimulus-response space by building neural encoding manifolds. We find that the different processing stages of the model (i.e., the feedforward encoder, recurrent, and readout modules) each exhibit qualitatively different representational structures in these manifolds. The recurrent module shows a jump in capabilities over the encoder module by 'pushing apart' the representations of different temporal stimulus patterns; while the readout module achieves biological fidelity by using numerous specialized feature maps rather than biologically plausible mechanisms. Overall, we present this work as a study of the inner workings of a prominent neural foundation model, gaining insights into the biological relevance of its internals through the novel analysis of its neurons' joint temporal response patterns.
toXiv_bot_toot
2025-09-25 11:26:02
#KI darf kein Black Box-Spielzeug für Großkonzerne bleiben – das fordert #Mistral AI und startet die Initiative „KI für Bürger“. Es geht um Transparenz, Teilhabe und die strategische Nutzung künstlicher Intelligenz zugunsten von Gesellschaft und Staat – statt „One Size fits all“-Lösungen aus der Cloud. W…
2025-10-14 13:15:18
LLMAtKGE: Large Language Models as Explainable Attackers against Knowledge Graph Embeddings
Ting Li, Yang Yang, Yipeng Yu, Liang Yao, Guoqing Chao, Ruifeng Xu
https://arxiv.org/abs/2510.11584
2025-09-30 13:15:31
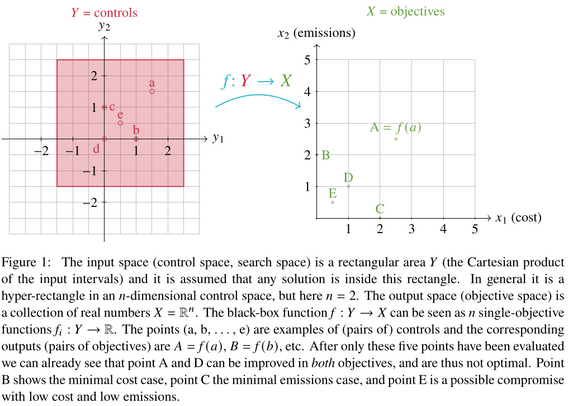
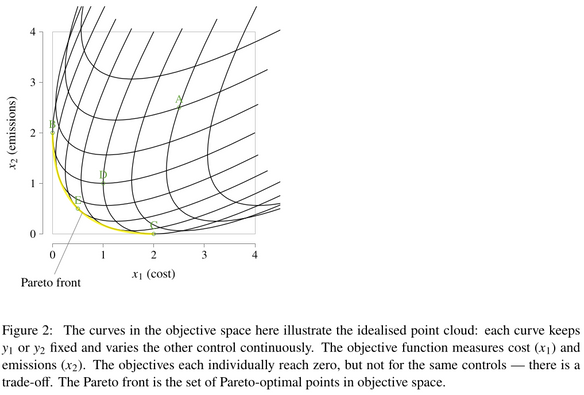
🌍 The climate crisis demands urgent action. But which actions are best?
Decision makers face tough trade-offs:
Policy A lowers emissions at home but increases reliance on imports.
Policy B cuts emissions long-term but raises unemployment short-term.
Policy C boosts jobs now but increases emissions in the near term.
None of these choices are simple. A policy that looks good locally may increase global emissions, or its effects may depend on what other countries d…
2025-10-09 09:06:21
Developing a Cost-Effective Spectrometer: A Practical Approach
Mohammad Tahsin Alam, Zafrin Jahan Nikita, Yasir Mahmud, Rafichha Yeasmin, Fairuz Darimi Bushra, Sheikh Hasib Cheragee, Redwanul Talukder Zeem
https://arxiv.org/abs/2510.06703
2025-09-23 08:31:00
Semi-Analytic Solutions to the Noh Problem with a Black Box Equation of State
Seth Gerberding, Jeff Peterson, Jim Ferguson, Scott Ramsey
https://arxiv.org/abs/2509.16766 https:/…
2025-11-11 09:06:47
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-09-25 00:30:01
On The Road - To Xi’An/ Departure II 🔜
在路上 - 去西安/ 离 II 🔜
📷 Pentax MX
🎞️Kodak Double-X 5222
#filmphotography #Photography #blackandwhite
2025-10-03 21:26:26
In Praise of RSS and Controlled Feeds of Information
https://blog.burkert.me/posts/in_praise_of_syndication/
2025-10-07 09:52:32
TCR-EML: Explainable Model Layers for TCR-pMHC Prediction
Jiarui Li, Zixiang Yin, Zhengming Ding, Samuel J. Landry, Ramgopal R. Mettu
https://arxiv.org/abs/2510.04377 https://…
2025-10-14 11:48:48
ArtPerception: ASCII Art-based Jailbreak on LLMs with Recognition Pre-test
Guan-Yan Yang, Tzu-Yu Cheng, Ya-Wen Teng, Farn Wanga, Kuo-Hui Yeh
https://arxiv.org/abs/2510.10281 htt…
2025-10-09 10:46:01
Clifford testing: algorithms and lower bounds
Marcel Hinsche, Zongbo Bao, Philippe van Dordrecht, Jens Eisert, Jop Bri\"et, Jonas Helsen
https://arxiv.org/abs/2510.07164 ht…
2025-09-29 09:39:27
Decoding Deception: Understanding Automatic Speech Recognition Vulnerabilities in Evasion and Poisoning Attacks
Aravindhan G, Yuvaraj Govindarajulu, Parin Shah
https://arxiv.org/abs/2509.22060
2025-12-11 18:53:38
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-11-04 21:32:35
2025-10-06 09:49:39
Onto-Epistemological Analysis of AI Explanations
Martina Mattioli, Eike Petersen, Aasa Feragen, Marcello Pelillo, Siavash A. Bigdeli
https://arxiv.org/abs/2510.02996 https://
2025-10-02 10:16:51
Effectiveness of Reconfigurable Intelligent Surface in Multipath Fading Channel
Hasnul Hashim
https://arxiv.org/abs/2510.00838 https://arxiv.org/pdf/2510.0…
2025-10-01 14:41:53
Replaced article(s) found for cs.CC. https://arxiv.org/list/cs.CC/new
[1/1]:
- Black-Box Crypto is Useless for Pseudorandom Codes
Sanjam Garg, Sam Gunn, Mingyuan Wang
2025-10-02 09:01:21
Privately Estimating Black-Box Statistics
G\"unter F. Steinke, Thomas Steinke
https://arxiv.org/abs/2510.00322 https://arxiv.org/pdf/2510.00322…
2025-10-08 10:38:29
NeST-BO: Fast Local Bayesian Optimization via Newton-Step Targeting of Gradient and Hessian Information
Wei-Ting Tang, Akshay Kudva, Joel A. Paulson
https://arxiv.org/abs/2510.05516
2025-10-10 09:01:09
Surrogate Graph Partitioning for Spatial Prediction
Yuta Shikuri, Hironori Fujisawa
https://arxiv.org/abs/2510.07832 https://arxiv.org/pdf/2510.07832
2025-10-07 11:19:42
Introduction to Interpolation-Based Optimization
Lindon Roberts
https://arxiv.org/abs/2510.04473 https://arxiv.org/pdf/2510.04473
2025-09-22 00:30:00
On The Road - To Xi’An/ Beings II 👁️🗨️
在路上 - 去西安/ 灵 II 👁️🗨️
📷 Pentax MX
🎞️Kodak Double-X 5222
#filmphotography #Photography #blackandwhite
2025-12-08 12:50:25
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-09-24 03:18:17
Select your desktop environment... IF YOU DARE
#CatsOfMastodon
2025-09-29 09:00:47
SADA: Safe and Adaptive Inference with Multiple Black-Box Predictions
Jiawei Shan, Yiming Dong, Jiwei Zhao
https://arxiv.org/abs/2509.21707 https://arxiv.o…
2025-10-03 10:36:01
Activation-Deactivation: A General Framework for Robust Post-hoc Explainable AI
Akchunya Chanchal, David A. Kelly, Hana Chockler
https://arxiv.org/abs/2510.01038 https://…
2025-09-30 10:54:41
Walk the Talk: Is Your Log-based Software Reliability Maintenance System Really Reliable?
Minghua He, Tong Jia, Chiming Duan, Pei Xiao, Lingzhe Zhang, Kangjin Wang, Yifan Wu, Ying Li, Gang Huang
https://arxiv.org/abs/2509.24352
2025-10-02 11:08:21
Eliciting Secret Knowledge from Language Models
Bartosz Cywi\'nski, Emil Ryd, Rowan Wang, Senthooran Rajamanoharan, Neel Nanda, Arthur Conmy, Samuel Marks
https://arxiv.org/abs/2510.01070
2025-10-03 07:34:30
Fine-Tuning Jailbreaks under Highly Constrained Black-Box Settings: A Three-Pronged Approach
Xiangfang Li, Yu Wang, Bo Li
https://arxiv.org/abs/2510.01342 https://
2025-10-01 11:40:27
ProfVLM: A Lightweight Video-Language Model for Multi-View Proficiency Estimation
Edoardo Bianchi, Jacopo Staiano, Antonio Liotta
https://arxiv.org/abs/2509.26278 https://
2025-10-22 15:10:58
Series D, Episode 05 - Animals
VILA: Are we expecting trouble on this trip?
AVON: A federation patrol attacked Scorpio at Bucol Two. They might wonder what it was doing there in the first place. I would in their position.
https://blake.torpidity.net/m/405/287 B7B4
2025-11-22 02:22:07
2025-10-02 10:41:41
Activation-Deactivation: A General Framework for Robust Post-hoc Explainable AI
Akchunya Chanchal, David A. Kelly, Hana Chockler
https://arxiv.org/abs/2510.01038 https://…
2025-10-07 08:54:12
Quantile-Scaled Bayesian Optimization Using Rank-Only Feedback
Tunde Fahd Egunjobi
https://arxiv.org/abs/2510.03277 https://arxiv.org/pdf/2510.03277…
2025-10-03 11:00:31
GRACE: A Language Model Framework for Explainable Inverse Reinforcement Learning
Silvia Sapora, Devon Hjelm, Alexander Toshev, Omar Attia, Bogdan Mazoure
https://arxiv.org/abs/2510.02180
2025-10-07 10:06:02
Modular and Adaptive Conformal Prediction for Sequential Models via Residual Decomposition
William Zhang, Saurabh Amin, Georgia Perakis
https://arxiv.org/abs/2510.04406 https://…
2025-09-25 08:01:42
Knock-Knock: Black-Box, Platform-Agnostic DRAM Address-Mapping Reverse Engineering
Antoine Plin, Lorenzo Casalino, Thomas Rokicki, Ruben Salvador
https://arxiv.org/abs/2509.19568
2025-09-29 11:20:17
Where MLLMs Attend and What They Rely On: Explaining Autoregressive Token Generation
Ruoyu Chen, Xiaoqing Guo, Kangwei Liu, Siyuan Liang, Shiming Liu, Qunli Zhang, Hua Zhang, Xiaochun Cao
https://arxiv.org/abs/2509.22496
2025-10-27 16:46:26
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-10-01 11:30:27
LLM Agents for Knowledge Discovery in Atomic Layer Processing
Andreas Werbrouck, Marshall B. Lindsay, Matthew Maschmann, Matthias J. Young
https://arxiv.org/abs/2509.26201 https…
2025-09-30 14:10:10
Circuit Distillation
Somin Wadhwa, Silvio Amir, Byron C. Wallace
https://arxiv.org/abs/2509.25002 https://arxiv.org/pdf/2509.25002
2025-10-07 08:14:41
Explainable but Vulnerable: Adversarial Attacks on XAI Explanation in Cybersecurity Applications
Maraz Mia, Mir Mehedi A. Pritom
https://arxiv.org/abs/2510.03623 https://…
2025-09-26 10:20:41
Learning Conformal Explainers for Image Classifiers
Amr Alkhatib, Stephanie Lowry
https://arxiv.org/abs/2509.21209 https://arxiv.org/pdf/2509.21209
2025-09-26 10:28:51
LAVA: Explainability for Unsupervised Latent Embeddings
Ivan Stresec, Joana P. Gon\c{c}alves
https://arxiv.org/abs/2509.21149 https://arxiv.org/pdf/2509.21…
2025-10-06 08:34:39
Privacy in the Age of AI: A Taxonomy of Data Risks
Grace Billiris, Asif Gill, Madhushi Bandara
https://arxiv.org/abs/2510.02357 https://arxiv.org/pdf/2510.…
2025-10-20 10:09:39
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-09-30 09:01:51
Unsupervised Conformal Inference: Bootstrapping and Alignment to Control LLM Uncertainty
Lingyou Pang, Lei Huang, Jianyu Lin, Tianyu Wang, Akira Horiguchi, Alexander Aue, Carey E. Priebe
https://arxiv.org/abs/2509.23002
2025-09-25 10:39:42
Smaller is Better: Enhancing Transparency in Vehicle AI Systems via Pruning
Sanish Suwal, Shaurya Garg, Dipkamal Bhusal, Michael Clifford, Nidhi Rastogi
https://arxiv.org/abs/2509.20148
2025-11-19 05:34:05
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-09-30 11:24:31
Symmetry-Aware Bayesian Optimization via Max Kernels
Anthony Bardou, Antoine Gonon, Aryan Ahadinia, Patrick Thiran
https://arxiv.org/abs/2509.25051 https://
2025-10-19 17:13:37
🇺🇦 Auf radioeins läuft...
Automatic:
🎵 Black Box
#NowPlaying #Automatic
https://blackflooddixon.bandcamp.com/track/peppermint-box
https://open.spotify.com/track/45c2puZgmaC23MaKgeHda2
2025-09-29 09:53:48
Backdoor Attribution: Elucidating and Controlling Backdoor in Language Models
Miao Yu, Zhenhong Zhou, Moayad Aloqaily, Kun Wang, Biwei Huang, Stephen Wang, Yueming Jin, Qingsong Wen
https://arxiv.org/abs/2509.21761